15 min to read
From Zero to Hero: Setting Up Your Kali Linux VM Like a Pro
A step-by-step guide to setting up a freshly installed Kali Linux virtual machine for optimal pentesting efficiency and customization.

Starting fresh in a new Kali Linux environment can feel a bit like unboxing a shiny new gadget—it’s exciting, full of potential, and, if you’re like me, immediately in need of some custom tweaks and setups. Whether you’re spinning up your environment to kick off a new pentesting project or just to explore new tools and techniques, getting your environment set up the right way is key to staying efficient. In this post, I’m going to walk you through my top ten steps for prepping a Kali Linux VM from the moment you spin it up. Whether you’re a seasoned pentester looking for a checklist refresher or a newcomer eager to learn the ropes, this guide is built to make your Kali journey smoother and more effective.
 1. Creating a New Account
1. Creating a New Account
The first thing you do on a new Kali Linux VM is well, log in! To do this you’ll use the kali:kali login that comes standard with every installation of Kali Linux. Using this account is considered a bad practice due to the predictability in the username and the password and because the username got sudo privileges by default. It’s therefore important that you create a new account that you’ll be working from when using the virtual machine. You also want to assign this account sudo privileges and add this account to the vboxsf group if you want this account to have access to your shared folders that you’ve specified in Virtual Box which allows you to transfer files between the virtual machine and the host.
# Add a new user
adduser k1ngdamien
# Give the newly created user sudo privileges
usermod -aG sudo k1ngdamien
# Add the newly created user to the vboxsf group
sudo adduser k1ngdamien vboxsf
Once the new account is created and the permissions are set, you should be good to go! Also make sure to change the default password of the “kali” account and change the password of the root user.
 2. Update and Upgrade
2. Update and Upgrade
Even though it is very likely you got the latest version of the Kali Linux image running, a lot of the software and tooling running on this image could already be outdated. It is therefore recommended to update and upgrade the software in the Kali Linux environment. Ensuring that your software is up-to-date with the latest security patches and bug fixes is very important in an environment where you’ll likely work with confident data and information. Running an update and upgrade also helps with the system optimization and the repository synchronization, making sure that the system knows about the latest versions available in the repositories.
# Updating and Upgrading
sudo apt update && sudo apt upgrade -y
# Setting up the correct Linux Headers
sudo apt install linux-headers-$(uname -r)
 3. Customize the Account
3. Customize the Account
Now that we have a custom account and an updated environment, it is time to do some account customization. From this point forward, this is where your own personal preferences come into play. The following steps describe my preferences in terms of software, tooling and plugins. To start off, account customization. My preference in terms of the shell that I am using in Z shell (or Zsh). I feel that it offers more that the traditional bash shell especially with stuff like Oh My Zsh. With creating a new account the default shell that is assigned is the bash shell, we want to change this to a Z shell by executing the following command: chsh -s /bin/zsh. To check if this command worked successfully you’ll have to reboot your system and run $SHELL to see if you have the correct shell type now.
# Switch to Z Shell
chsh -s /bin/zsh
# Check your current shell type
echo $SHELL
Now that we’re using Z Shell, we could make some aliases that’ll make our life easier. An alias is like your personal shortcut to getting things done faster. Think of it as creating your own custom command that takes a long, complex string of instructions and condenses it into one simple word or phrase. I always like to make aliases for the OpenVPN connections I need to run to do labs or machines on Hack the Box and TryHackMe. Any repetitive command that is long to type is a great candidate to turn into an alias! You can add aliases by editing the ~/.zshrc file and adding the following lines to the file:
# Adding CTF aliases to zshrc file
alias htb-lab='sudo openvpn <path-to-.ovpn-file>'
alias thm-lab='sudo openvpn <path-to-.ovpn-file>'
 4. Terminal Multiplexer Setup
4. Terminal Multiplexer Setup
A terminal multiplexer is an essential tool for anyone who relies heavily on the command line, especially us penetration testers. It allows you to manage multiple terminal sessions from a single screen, split windows, and detach or reattach to sessions seamlessly. This means you can run various tasks like network scans, exploit scripts, and maintain reverse shells in an organized way. My terminal multiplexer of choice is tmux. It was the first multiplexer I used and I haven’t had any complaints yet, the configuration to customize it is easy to do and it is easy to understand and learn. I use the following configuration mainly based on ippsec’s tmux configuration in my configuration file (~/.tmux.conf):
# Customized Tmux configuration based on ippsec's config file (~/.tmux.conf).
#set prefix
set -g prefix C-a
bind C-a send-prefix
unbind C-b
set -g history-limit 100000
set -g allow-rename off
bind-key j command-prompt -p "Join pane from:" "join-pane -s :'%%'"
bind-key s command-prompt -p "Send pane to:" "join-pane -s :'%%'"
set-window-option -g mode-keys vi
run-shell /opt/tmux-logging/logging.tmux
 5. Customize Firefox
5. Customize Firefox
For my web application penetration tests I mainly use Firefox (or the build in Burp browser) to access the target and route my traffic through Burp. To route my traffic through Burp Suite I make use of the FoxyProxy extension. FoxyProxy is a browser extension that simplifies the process of managing and switching between multiple proxy server configurations. The following image shows the configuration for FoxyProxy.
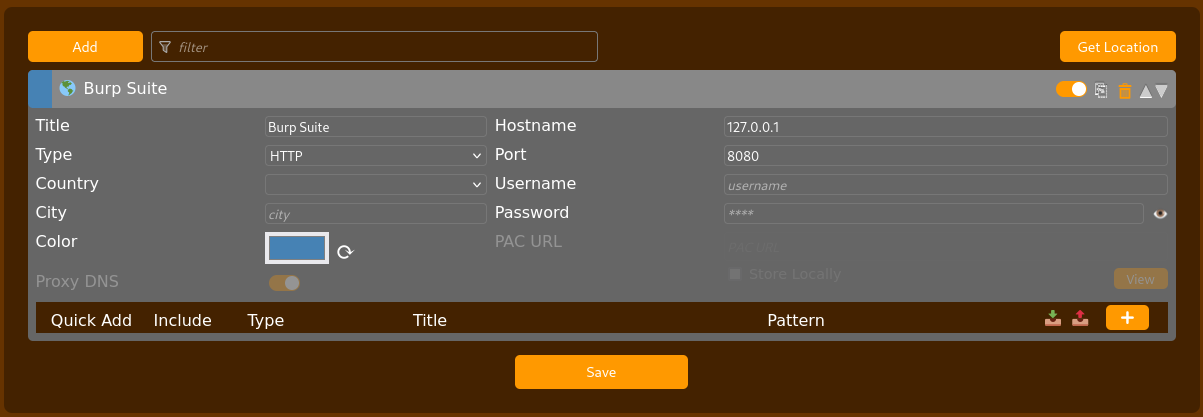
Another extension I like to use is the Wappalyzer extension. The Wappalyzer extension is a tool used to identify the technologies used on websites. It is widely used by developers, penetration testers, and digital marketers to gather information about the technological stack of a website. There’s also plenty of tools that do this in Kali itself, but I like this to get a quick overview what a web application is running on and to see if there are outdated technologies used that are findings in themselves.
 6. Install and Customize Burp Suite
6. Install and Customize Burp Suite
Burp Suite is the go to tool for web application penetration testing. Burp Suite offers a “suite” of tools that make finding and exploiting vulnerabilities a breeze, from intercepting and modifying HTTP traffic to automating scans. One of the best things about Burp Suite is the ability to download, import or create your own extensions that’ll make Burp Suite an even more broad tool. To fully optimize Burp Suite, the first step is to install it. I personally use Burp Suite Professional, but if you’re new to offensive cybersecurity or won’t be using Burp Suite often, the Community version will also suffice. Burp Suite Community is present on Kali Linux by default, the professional version can be downloaded here. Once you got Burp Suite installed and your FoxyProxy on in Firefox, it’s time to set the proper certificate in Firefox so you do not run into issues when routing traffic through Burp Suite. A detailed explanation can be found here which does a better job in explaining it than I ever could.
In order to use extensions in Burp Suite, most of them require Jython. The Jython project provides implementations of Python in Java, providing to Python the benefits of running on the JVM and access to classes written in Java. Installing it is rather simple you can download the .jar here and use the following command to install Jython with the .jar file: java -jar jython-installer-2.7.3.jar.
Now for the extensions, I got multiple extensions that I use during every test which I highly recommend for you to use. Authorize which is a great extension for testing authorization vulnerabilities which is usually one of the more time consuming tasks during a penetration test. Another good extension is JS Miner, this tool tries to find interesting stuff inside static files; mainly JavaScript and JSON files. Logger++ is also an incredible tool that extends the capabilities of the normal Burp Suite logger by providing more details. This extension is very resource heavy so keep that in mind. The last noteworthy extension is the JWT Editor. This extension allows the editing, signing, verifying, encrypting and decrypting of JSON Web Tokens (JWTs).
 7. Install GO for Tooling
7. Install GO for Tooling
A lot of tooling that I use for my day-to-day testing require Go. Go, also known as Golang, is a powerful open-source programming language developed by Google that’s known for its speed, simplicity, and efficient concurrency. This makes it a perfect programming language for writing tooling. There are a lot of different tutorials online that will tell you how to install GO specifically for Kali Linux but I found that most of them make it too difficult or are just unclear in general. Installing Go is very simple by following these commands below:
# Install the package
sudo apt install -y golang
# Add the following information to your .zshrc (or .bashrc if using bash)
export GOPATH=/home/<usr>/go-workspace
export GOROOT=/usr/lib/go
PATH=$PATH:$GOROOT/bin:$GOPATH/bin
# Reload your .zshrc file
source .zshrc
 8. Install Web Tooling
8. Install Web Tooling
Installing the proper tooling for your assessments and tests is one of the more important things of setting up the environment. When you’re doing a penetration test you quickly want to have the right tooling available and be familiar with it. For this part of the setup I have picked three areas in which I usually do penetration tests on or where I want to improve my penetration testing skills. The first of these is web application penetration testing. We already discussed Burp Suite which is the most commonly used tool for web application pentesting but there is a whole world of interesting tools that deserve attention.
The first bunch of tools all belong to ProjectDiscovery. ProjectDiscovery is an open source powered security company that offer a large collection of interesting tools such as Subfinder, Katana, HTTPX and their most famous tool Nuclei. Subfinder is an amazing subdomain discovery tool that returns valid subdomains for websites, using passive online sources. This means it doesn’t interact with the domain itself. Katana is a lightweight web crawler that’s designed for speed and depth, making it the perfect tool for web application penetration testing. It helps streamline the discovery phase and provides a clearer attack surface for further probing and exploitation. Once you’ve got a good list of potential subdomains of the target, you can use httpx. httpx is designed to probe thousands of URLs with ease, checking for live hosts and fetching valuable information such as response codes, headers, and technologies. Nuclei is a versatile security/vulnerability scanner that can look for a broad variety of vulnerabilities. Nuclei is too big to
# Installing SubFinder with Go
go install -v github.com/projectdiscovery/subfinder/v2/cmd/subfinder@latest
# Installing Katana with Go
go install -v github.com/projectdiscovery/katana/cmd/katana@latest
# Installing HTTPX with Go
go install -v github.com/projectdiscovery/httpx/cmd/httpx@latest
# Installing Nuclei with apt
apt install nuclei
Tomnomnom is also an amazing tool creator that has a large variety of tools that are useful for web application pentesting but also other kinds of penetration testing. Some of my favourite tools that he has created are the following:
 9. Install API Tooling
9. Install API Tooling
When setting up a new Kali Linux environment for penetration testing, especially API penetration testing, having the right API-focused tools can make all the difference. Unlike typical web testing tools that focus on web page vulnerabilities, API tools dive deep into the nuts and bolts of how applications communicate, making them essential for probing RESTful, SOAP, and GraphQL endpoints for weaknesses. The following tools are some of my favorites for pentesting APIs:
-
Postman – Postman is a favorite for many penetration testers, allowing you to easily craft, send, and analyze API requests. It’s especially handy for exploring APIs and testing authentication. To install Postman on Kali Linux, execute the following command: sudo wget https://dl.pstmn.io/download/latest/linux64 -O postman-linux-x64.tar.gz && sudo tar -xvzf postman-linux-x64.tar.gz -C /opt && sudo ln -s /opt/Postman/Postman /usr/bin/postman.
-
HTTPie – A CLI-based tool that simplifies HTTP requests with a readable, JSON-based output. It’s fantastic for quickly testing APIs directly from the terminal and speeds up exploratory testing.
-
mitmproxy2swagger - mitmproxy2swagger is a handy tool for API testing that automatically generates Swagger documentation by capturing live API traffic, making it perfect for undocumented or poorly documented APIs. Working alongside mitmproxy, it intercepts the communication between client and server, then converts the detected endpoints, methods, and parameters into a Swagger (OpenAPI) spec file.
-
JWT_Tool - JWT_Tool is a powerful Python-based utility specifically designed for testing and exploiting JSON Web Tokens (JWTs), which are often used in web apps for authentication and data exchange. JWTs can be a critical security point, and jwt_tool helps penetration testers analyze, manipulate, and exploit these tokens to uncover vulnerabilities.
-
KiteRunner - Kiterunner is a powerful tool specifically designed to brute-force endpoints on web application APIs, making it invaluable for API enumeration and discovery in penetration testing. Unlike traditional directory brute-forcers, Kiterunner focuses on mapping APIs by identifying hidden or undocumented endpoints that may otherwise go unnoticed.
 10. Install Cloud Tooling
10. Install Cloud Tooling
One of the current subjects I am focussing on is Azure AD testing. For Azure Active Directory (Azure AD) testing, a few specialized tools can help you navigate the complexities of cloud identity and access management. Azure AD tooling focuses on probing the unique authentication, identity, and access control systems within Microsoft’s cloud environment, which is quite different from traditional, on-premise Active Directory (AD) tooling.
-
MicroBurst – This PowerShell toolkit helps enumerate Azure environments, perform password spraying, and analyze permissions. While built in PowerShell, it can be run on Kali with PowerShell installed, offering cloud-focused recon capabilities.
-
ROADtools – Specifically designed for Azure AD, ROADtools includes modules for authenticating to Azure AD, dumping directory information, and mapping out the Azure AD environment. It’s a comprehensive suite that can reveal risky permissions and user privileges.
-
AADInternals – Another PowerShell-based tool that can be used on Kali, AADInternals supports tasks like token manipulation, privilege escalation, and Azure AD recon. It’s particularly helpful for testing app registration permissions and privileged accounts.
-
Azucar – This Python tool provides automated enumeration and recon on Azure, reporting back on misconfigurations or weaknesses. It’s lightweight, easy to use, and great for quick scans on a new Azure target.
 Conclusion
Conclusion
Setting up a Kali Linux VM isn’t just about downloading the image and logging in—it’s about creating a tailored environment where every tool and shortcut boosts your efficiency as a pentester. From basic OS tweaks to installing specialized tools like Subfinder for subdomain discovery or Burp Suite for web application testing, each step adds another layer to your setup, giving you the right capabilities for any security assessment. Remember, building an efficient pentesting setup is as much about the right tools as it is about knowing how to use them effectively. As you work through each project, you’ll find that having this foundational setup pays off by letting you focus more on testing and less on tool configuration.

Comments