9 min to read
The World of Wordlists
An article on how to make the most out of custom password wordlists and how to customize them perfectly for the targets in your assessments!

During one of my recent engagements, the client tasked me with assessing the strength of their passwords by providing me with password hashes to see if they can be cracked. Passwords and password cracking have always interested me, usually you encounter them as small challenges in Capture the Flags (CTFs) or when you retrieve a set of hashes during a Red Team engagement. So as you can imagine, I was very eager to try and see if these hashes were crackable and too see what kind of passwords were being used in 2024 on a day to day basis. With the introduction of stronger password policies I was always under the impression that cracking hashes has become an obsolete process, but I was surprised with the state of passwords even with a good password policy in place.
 Enter the world of wordlists
Enter the world of wordlists
To make the most out of password cracking or fuzzing web applications you need a good and suitable wordlist, because you wouldn’t use a wordlist filled with common passwords to fuzz directories of a web application. There are tons of publicly available wordlists online that are highly recommended for different situations. In my opinion, the best collections of wordlists are provided by Daniel Miessler’s SecLists1 and by Krypton2 both available on their respective GitHubs pages. There are wordlists for almost everything you can fuzz, guess or crack. Think about parameters for web applications, directories, usernames and passwords.
One of the best known wordlists is the “rockyou.txt” wordlist. This wordlist contains close to 15 million passwords that are based on actual real-life passwords. Back in 2009, a company called Rock You was hacked. Whilst this isn’t uncommon, the problem was that Rock You stored all their user passwords unencrypted, in plain text for the attacker to see. This list has been a great resource for security researchers and pentesters to test the strength of passwords within their systems. But of course it has also been used by black hat hackers who want to find quick wins and take over accounts with simple credentials.
Based on the location your client is based during the assessment, there’s also other interesting wordlists you can you besides the standard rockyou wordlist. There are tons of language specific wordlists that single out common passwords in a specific language. Since I am based in the Netherlands, I often make use of “dutch.txt” and “dutch-passwords.txt” wordlists. Another perk of these wordlists is that they’re a lot smaller than rockyou.txt which could help when you’re dealing with less GPU/CPU capabilities when running a cracking tool locally.
 Customizing the perfect wordlist
Customizing the perfect wordlist
While the existing wordlists offer huge amounts of passwords, most companies that offer some sort of awareness trainings and have a password policy in place will tell you not to use these basic passwords or won’t even allow you to use these basic passwords. So does this mean that people switch to more advanced, uncrackable passwords? Absolutely not. People will do the bare minimum to pass the password requirements set up in a policy. Nowadays most password policies will force you to:
- Have a minimum amount of characters
- Have a capital letter in the password
- Have a number in the password
- Have a special character in the password
Whilst from the naked eye this looks like a solid password policy, people will do the bare minimum and you will end up with password like: Jordan21!, Amsterdam020? and Seven77@. These are common passwords with a slight variation, because if you make a password too difficult, you might forget your own password! Whilst these passwords will (likely) not be part of your standard wordlists, there are still easy ways to crack them with something called rules in the Hashcat tool which will be discussed in the next chapter.
Okay so now we know what passwords look like when a common password policy is enforced, but how do you determine the main words passwords are based around (e.g. Jordan, Amsterdam or Seven)? People will often create passwords out of places, items or people they are familiar with and won’t easily forget. It is very common people create passwords out of the names of their parents, their children, other members of their family, their pets, their hometowns, you get the picture. Based on the time you have for your assessment or the scope you have, it is relatively easy information to retrieve through Open Source Intelligence (OSINT). Open Source Intelligence will be covered in a future blog post but in short, OSINT is the collection and analysis of information that is gathered from public and open sources. In addition, when you find interesting information you could use tools like CUPP - Common User Password Profiler3 to create a set of potential passwords.
Another technique I implemented was gathering specific terms that are applicable to the client. You can think of the company name, variations on this name, abbreviations, the location of the office, departments, roles, etc. This later turned out to be a great success during the cracking phase. The way I approached this was first checking for all subdomains associated with the client through sublister, checking which ones were active and based on all the subdomains that were up, find suitable ones that have words that would make sense to put in a wordlist. To extract the words from a subdomain I used two tools, CeWL by Digininja4 and Skweez by Edermi5. Where CeWL is the broader, more extensive tool and Skweez is the faster, more lightweight tool. In the example below, you can see the usage of Skweez on the target domain. This results in a list of 1388 interesting words from https://k1ngdamien.com/.
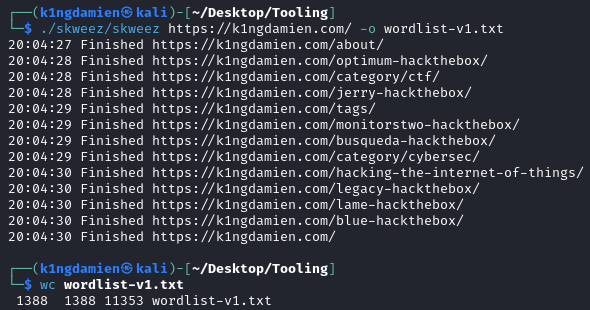
You can combine all the lists from different domains, lists you made during your OSINT phase into one big, custom made wordlist suitable for your engagement!
 Hashcat and cracking passwords
Hashcat and cracking passwords
So now that we got a wordlist full of potential passwords, what is the next step? Cracking! There are multiple tools to crack password hashes but the two biggest ones are John the Ripper6 and Hashcat7. Depending on the situation and the hardware at your disposal, both tools offer different pros and cons. My personal preference is Hashcat since it offers great GPU support, so I’ll be using that for the example. With the wordlist at our disposal and some made up hashes to crack you’d think we’re ready to get cracking. In theory, yes. You’d be able to run Hashcat and find potential matches between the hashes and the wordlist. But the chance in finding a positive match is small because currently the wordlist does not contain any special characters.
Now, you could manually add numbers and special characters to the wordlist but with a wordlist of a decent size, this will be a time consuming and practically impossible task. To solve this, there is the ability to add a rule file as a parameter in your hashcat command. This rule file can be fully customized based on the passwords patterns that you want to cover on the words in your wordlist(s). Do you want to add numbers to the back or the front of words? Add special characters, switch letters around, capital letters, small letters it is all possible. You can make your own set of rules or you can look around GitHub for already existing Hashcat rules. One of the bigger, more known rules is the “One Rule to Rule them All”8 created by NotSoSecure. Anyone who’s familiar with Lord of the Rings surely has their interest peaked even more now. This rule covers a huge amount of potential password patterns but can also be used to draw inspiration for your own rule list. But you can also look for the syntax used for rules on the Hashcat website here.
With everything set it is time to run the following command to start password cracking:
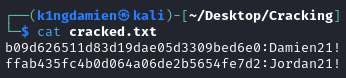
hashcat -m 1000 hashes.txt wordlist-v1.txt -r OneRuleToRuleThemAll.rule -o cracked.txt
Since I got a decent GPU and the size of the original wordlist is not that big, it’s done pretty quickly with both hashes I provided being cracked:
 The uncrackable password
The uncrackable password
Well with all the possibilities that come with hash cracking, you might think that every hash is crackable and no password is safe. While in theory this is true, the reality of it is that if you have a longer and more complex password, it’ll take too long to crack in most cases. But the key to having a practically uncrackable password is making it long, complex and preferably not relatable to you as a person in any way. With this I mean that it’s time to stop using the names of your children, parents, partners, friends or pets as you passwords but to create passwords that have nothing to do with you. Add some complexity in it with a lot of random characters, a difference in capital letters and lower case letters and you’ll have a solid password.
Nowadays a lot of people also use password managers to store their passwords and to even generate passwords for them. In a future blog post I’ll cover these password managers and how safe and good they are at generating passwords, so stay tuned!


Comments