8 min to read
Hacking the Internet of Things (IoT)
An article on Shodan.io, the way it works and some interesting and useful queries for red team engagement and security researchers looking to kick off their Shodan adventures!
A couple of weeks ago Shodan.io offered the premium version of their service with a ninety percent discount, going down from $50 to just $5. With this huge discount, the tool will have a lot of new users experiencing the premium features for the first time or completely new users to the tool itself. I myself have taken advantage of this discount and have been diving into the world of Shodan, I used Shodan in the past before but with my new premium account, I decided to dive deeper into it. This article focusses on what Shodan exactly is, what you can do with it and some interesting queries that could come in handy for bug bounty hunters and red teams doing engagements.
 The ins and outs of Shodan.io
The ins and outs of Shodan.io
Shodan is often described as the search engine for the Internet of Things (IoT) which, throughout this article, will be asserted more and more. Shodan is a search engine like Google but instead of looking for websites, it searches for devices that are connected to the internet. The range of these devices is massive, it could be IoT devices like refrigerators to thermostats, routers to servers all the way to government systems like powers plants and transportation systems. As you can see, if the device is internet-facing and isn’t properly protected, Shodan will pick it up.
Shodan started off as a hobby project by a young software engineer named John Matherly. He figured out an interesting way to map all devices connected to the internet by constantly crawling the web with randomly generated IP addresses. The public release of Shodan came quite a bit later, in 2009. While Shodan obviously is a great tool to use for security researchers, red teams on an engagement and ethical hackers, this tool was and still is used frequently by malicious hackers to gain intelligence on potential targets for upcoming attacks.
 How does Shodan work and what can you find on Shodan?
How does Shodan work and what can you find on Shodan?
In short, Shodan.io works by sending out multiple connection requests to every IP-address that you could think of. Based on the information it gets back from these connection requests, it indexes the information. Imagining every possible IP address along with every port available on these IPs (65535), you could see the huge amount of data involved. Shodan is constantly sending out probes to these IP addresses and ports to gather information, in the form of banners that contain metadata about the target IP and port. These banners can provide a range of information like the device name, IP address, the port the service is on, the service itself, the organization behind the IP and the location.
But what exactly can Shodan.io detect and how? Well the how will be discussed below but the what can range from a ton of things. As mentioned previously, the main things found and detected are routers, services and IoT devices such as:
- Security cameras
- Traffic lights
- Internet routers
- Billboards
- FTP Servers
- And much more!
This is just the tip of the iceberg of possible query results on Shodan.io. The deeper you dig and the more sophisticated your queries become, the more detailed the results will be. Now knowing what you can expect from Shodan, it is time to get to the fun part of trying out different queries and seeing the results of them. The list compiled here are just a handful of queries that I found fun and enjoyable to try out but there are thousands of queries that you can use and customize to find what you’re looking for!
DISCLAIMER: Be careful when connecting to devices that are pointed out and shown on Shodan. Just because it is available doesn’t mean that gives you the right to access it.
 1. Secrets in HTML Body
1. Secrets in HTML Body
Secrets present in the source code is a constantly increasing issue within the development space. Thankfully there are a lot of solutions present to allow the removal of hard-coded secrets and turn them into environment secrets. However, sometimes there are still some hard-coded secrets present within HTML bodies. Hard-coded secrets come in many forms and can be stored in HTML bodies, the following queries will highlight three sorts of secrets that can be found inside of HTML bodies with the help of Shodan!
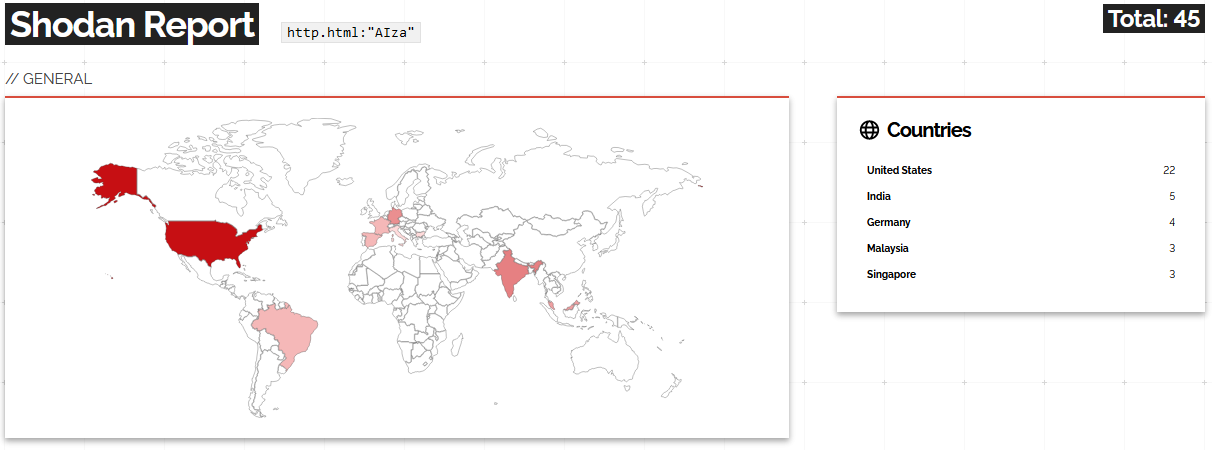
The above query looks for hard-coded Slack keys in the HTML body. As you can see from the results below the amount of hard-coded Slack Keys is very little only clocking in at six counts at the time of scanning.
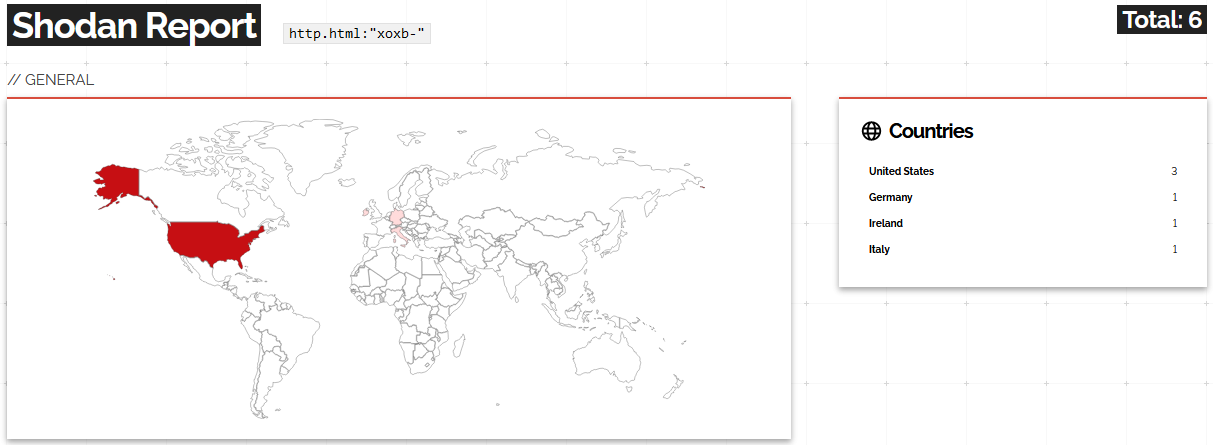
The above query looks for hard-coded Amazon AWS keys in the HTML body. Compared to the Slack keys query from earlier, this has more results and also has results outside of the United States and Europe.
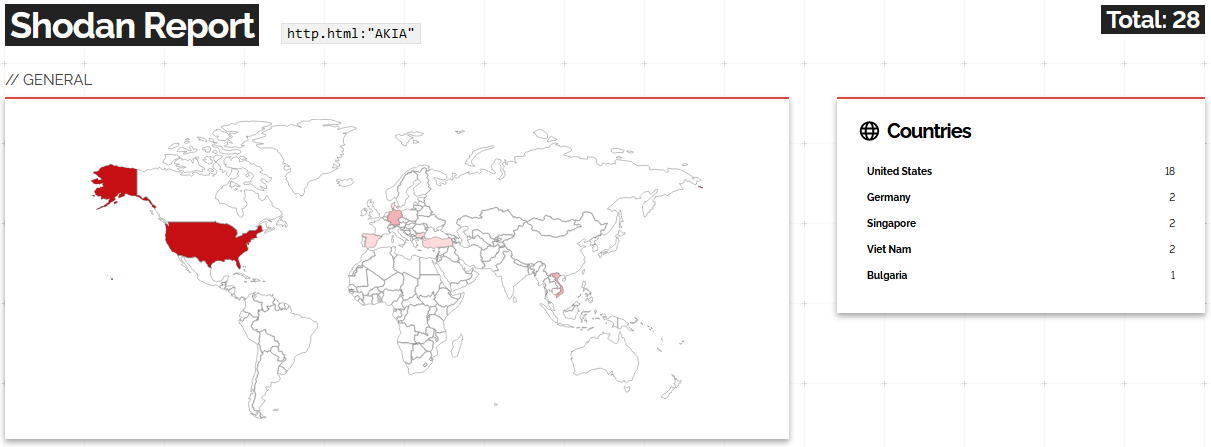
The above query looks for hard-coded Google Maps keys in the HTML body. This one has by far the most amount of findings compared to the other two entries and is present globally.
 2. Cameras on Shodan
2. Cameras on Shodan
Cameras and the Internet of Things, it’s almost impossible to not include these two in one sentence. The amount of cameras connected to the internet has increased massively and with their price dropping in general, the amount of cameras keeps increasing. Most cameras come with a default password that a lot of people tend to change, but not everybody. Default credentials for certain cameras and models still work perfectly fine. What is worse is that these cameras are internet-facing, making them exposed to the internet. With the capabilities available with Shodan, it is pretty easy to find these exposed webcams with multiple different queries:
General query returning everything that contains the camera keyword: title:camera
General query returning any IoT device that identifies as a camera that has screenshots available: webcam has_screenshot:true
 3. Finding open FTP ports
3. Finding open FTP ports
The File Transfer Protocol (FTP) is a protocol which allows the (easy) exchange of files between different devices. FTP is usually ran on port 21. These days FTP is not used very often anymore due to the lack of encryption the service offers and the introduction of better and more secure alternatives which are available and are more widely used. This, however, doesn’t mean FTP is completely gone, it is still used all over the world. The following queries will highlight available FTP services that are reachable by us and in some cases, where Anonymous logins are allowed.
FTP Ports which are open and Login Successful port:21 “230 Login Successful”
A query that allows the login of the “Anonymous” account, giving partial access to the content on the FTP server: 230 ‘anonymous@’ login
 4. Finding services and their versions
4. Finding services and their versions
Shodan can also be used to find specific services and their versions. This can come in handy when a new CVE for a specific framework or service gets published and you want to get a quick overview of the effected versions that are being served online. For example, you can run a query to check on the usage of Wordpress and then specifically a certain version like 1.5.1. This will give you an overview of running Wordpress instances running version 1.5.1. In the case that there is a CVE up for that, you could find out who the IP belongs to and see if they have an active bug bounty program and report the vulnerability there, within the scope that they set out.
On the Shodan CLI you can type out the following query to get an overview of all instances of Wordpress: shodan count wordpress
To look for a specific version of Wordpress or any other similar service execute the following query: shodan count wordpress 1.5.1
To download the information you’ve just gathered run the following query on the CLI: shodan download
"wordpress 1.5.1"
 5. Public Directory Listing
5. Public Directory Listing
Public Directory Listing means that the webserver lists all the content the webserver has to offer (e.g. the directories). Having it listed out like that allows an attacker to easily navigate and browse all directories and files that are present on the webserver. This often results in sensitive files being exposed such as logs, reports, files and parts of the code. Directory listings themselves do not necessarily constitute a security vulnerability. Any sensitive resources within the web root should in any case be properly access-controlled, and should not be accessible by an unauthorized party who happens to know or guess the URL.
Query for general Directory Listing that looks for “Index Of /” in HTTP title.http.title:”Index Of /”
A query that Directory Lists the /admin directory, can cause huge data breaches http.title:”Index Of /admin”
A second general Directory Listing query that looks for “Directory Listing” in HTTP title.http.title:”Directory Listing”
These are just a few queries in a world of thousands of other interesting queries. There are a lot of resources available online that focus on specific devices and specifically on bug bounty. Executing these basic queries will give you a good idea of the tool in general and can kickstart you Shodan.io adventures!


Comments